The cornerstone of DevOps is Continuous Integration and Continuous Delivery (CI/CD). By providing automation and monitoring across the development lifecycle, continuous integration/continuous development (or deployment) adds value to software production.
The CI/CD pipeline is a set of procedures that software developers follow in order to work on smaller chunks of code and increase overall productivity and efficiency.
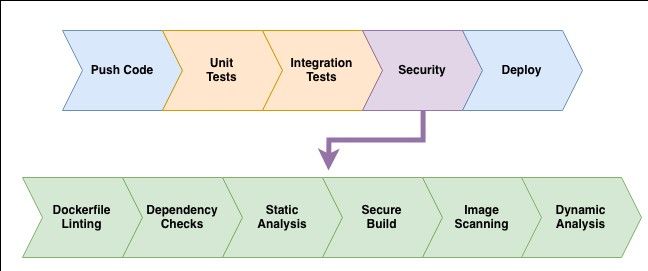
The fast-paced, automated, technology-driven environment swiftly devolves into a security-free zone. Security managers must strike a balance between protecting the pipeline and allowing for flexibility.
To avoid data breaches, the optimal way is to incorporate security into the development lifecycle. Below is a list of 13 best practices for managing CI/CD security.
1) Map Threats
Security threats exist at the intersections of several technologies. Due to the large number of automation tools, the CI/CD pipeline contains many vulnerable connection points.
To keep the pipeline secure at the seams, investigate potential vulnerabilities by locating them and installing extra security layers. Update and patch everything that connects to the manufacturing line on a regular basis, and ban any devices that don't match security requirements.
2) Secure Git
For CI/CD operations, version control solutions are a must-have. Because Git contains source code and intellectual property, misconfiguring it is a goldmine for attackers. In Git, an exposed vulnerability might have serious repercussions.
Two-factor authentication ensures secure access to the version control system. Educate developers about Git protocols and how to correctly use the .gitignore file.
3) Check Before Committing
Before committing any code to a repository, run a series of security tests. IDE plugins aid in the real-time detection of vulnerabilities in source code.
Peer-reviewing is also a good idea, especially for new coders. Create checklists for developers to utilize that will aid in the detection of compliance issues and data security. Make that there are no passwords, keys, tokens, or other sensitive data in the code or hardcoded.
4) Review Committed Code
After committing the code to a repository, go over it again. Without running the application, static code analysis tools can help provide insight into commits, generate reports, and provide helpful recommendations.
To ensure that problems are tracked and resolved, use bug tracking systems. Examine Git history for any suspicious activity and take appropriate action.
5) Monitor After Deployment
After you've installed the software, make sure to monitor it on a regular basis. Constant monitoring aids in the detection of undesired behaviors and provides useful data-based insights.
Create visual dashboards and alert mechanisms to make finding information easier.
6) Enforce Permissions
Although permissions slow down the testing process and are generally seen as a pain, make sure they are in place and that they are required. Developers must follow the rules and see task separation as a critical security feature.
Define access roles for each repository and only offer the information necessary to keep the pipeline running.
7) Secure Credentials
Make sure the credentials you use to access various development programs are safe. API tokens, SSH keys, passwords, and other types of certificates are available. Theft and data breaches are caused by improperly secured passwords.
Using key management platforms, enforce encryption key security in an automated manner. Password management software should be used, and security tokens should be rotated on a regular basis.
8) Clean Up
In a fast-paced atmosphere, it's common to move on to the next project before tidying up completely. Any temporary resources, such as virtual machines, containers, and processes, should be shut down.
To avoid having a backdoor and a potential point of unwanted entry, remove superfluous programs and utilities on a regular basis.
9) Implement IaC into the Pipeline
Infrastructure-as-Code (IaC) automates the setup of a standardized development and testing environment. IaC smoothly integrates into the DevOps process and assists in the creation of reusable configurations and scalable settings.
10) Scan for Open-Source Vulnerabilities
In order to create applications, open-source software is required. Such software, on the other hand, is prone to alterations and code upgrades. When these packages are updated, security risks develop, which have an indirect influence on the software that uses them.
Track components, files, and third-party tools to stay on top of open-source vulnerabilities. Use bug trackers and software composition analysis technologies to keep track of and evaluate all potential flaws.
11) Scan Infrastructure-as-Code Templates
IaC templates, such as Amazon CloudFormation, Azure Resource Manager, and Hashicorp Terraform, have been used by DevOps teams in conjunction with automation to quickly deploy, pull down, and manage infrastructure.
However, research conducted by Unit 42 Cloud Threat on IaC templates has indicated that a considerable proportion of them contain misconfigurations that do not conform with best practices or business security rules. As a result, vulnerable infrastructure is deployed, potentially resulting in exploits and breaches.
This issue can be solved by combining IaC template scanning and employing purpose-built security software that:
- Integrate seamlessly with existing DevOps processes including IDEs, PR, and CI/CD pipeline steps (as discussed above).
- Provide the scan results, the misconfiguration found, and any other relevant information needed to resolve the security issue.
12) Scan Kubernetes Application Manifests
The most common method for deploying apps on Kubernetes platforms is to declare all essential parameters in an application manifest, which is a YAML file. However, according to the same Unit 42 analysis, 42 percent of Docker containers based on open source software have unsafe defaults, which can lead to the deployment of risky containers and apps.
The National Institute of Standards and Technology's Application Container Security Guide (NIST SP 800-190) outlines controls for containers and containerized applications that should be included in order to secure these applications.
Incorporating security technologies that can scan for these controls into the DevOps IDE, PR processes, and CI/CD pipeline phases aids compliance and other best practices.
Security scans can discover insecure and non-compliant configurations before they are deployed, giving DevOps teams the opportunity to make the necessary modifications and updates.
A security scan, for example, can detect and notify an engineer if a container image is executed as the root user or with escalated capabilities. Detecting vulnerabilities at this early stage, rather than later after the container has been deployed, decreases team friction significantly.
13) Scan Kubernetes Application Manifests
Scanning the container image - a lightweight, standalone executable piece of software – is the third and last stage. Container images can be a major threat vector for containerized systems since they are frequently fetched from public repositories - essentially untrusted sources.
However, by doing an image scan when the image is produced and again in the CI/CD pipeline, it is possible to offer precise vulnerability information to DevOps teams at various stages during the development and deployment cycle with purpose-made security tools.
The scan results include a thorough description of the vulnerability, its severity, the status of a fix, and the software package version in which the vulnerability was fixed.
Conclusion
You should have a solid notion of how CI/CD security should work after reading this article. Finally, the best approach is to avoid inundating developers with security guidelines.
Rather, make security an automated component of the development process by including it into the pipeline.

