Container Registry Management: Securing and Optimizing Image Distribution for 40% Faster Deployments
Optimize container registry management for 40% faster deployments while maintaining security and reliability. Learn registry security best practices, image distribution optimization techniques, and management strategies that accelerate deployment pipelines and improve overall container workflows.

Introduction
Container registry management has become the backbone of modern DevOps operations, yet many organizations struggle with securing and optimizing their image distribution workflows. After working with dozens of enterprise teams, we've observed that poorly managed container registries can become significant bottlenecks, introducing security vulnerabilities and deployment delays that cost companies thousands of dollars in lost productivity.
The challenge extends beyond simple image storage. Organizations need comprehensive container registry management strategies that encompass security scanning, vulnerability assessment, lifecycle policies, and performance optimization. When implemented correctly, these practices can reduce deployment times by up to 40% while significantly strengthening security posture.
Throughout our experience implementing registry solutions for enterprise clients, we've developed proven methodologies that address both immediate operational needs and long-term scalability requirements. This comprehensive approach transforms container registries from potential security risks into strategic assets that accelerate development velocity while maintaining robust security standards.
The Container Registry Management Challenge
Modern enterprises face mounting pressure to accelerate software delivery while maintaining stringent security requirements. Traditional approaches to container image management often create significant operational friction, leading to deployment bottlenecks and security gaps that can cost organizations between $5,000 and $15,000 monthly in lost productivity and remediation efforts.
We recently worked with a financial services client managing over 2,000 container images across multiple development teams. Their existing registry lacked automated security scanning and proper lifecycle management, resulting in developers unknowingly deploying vulnerable images to production. The organization spent approximately $8,000 monthly on manual security reviews and emergency patches, while deployment cycles stretched to 3-4 weeks due to cumbersome approval processes.
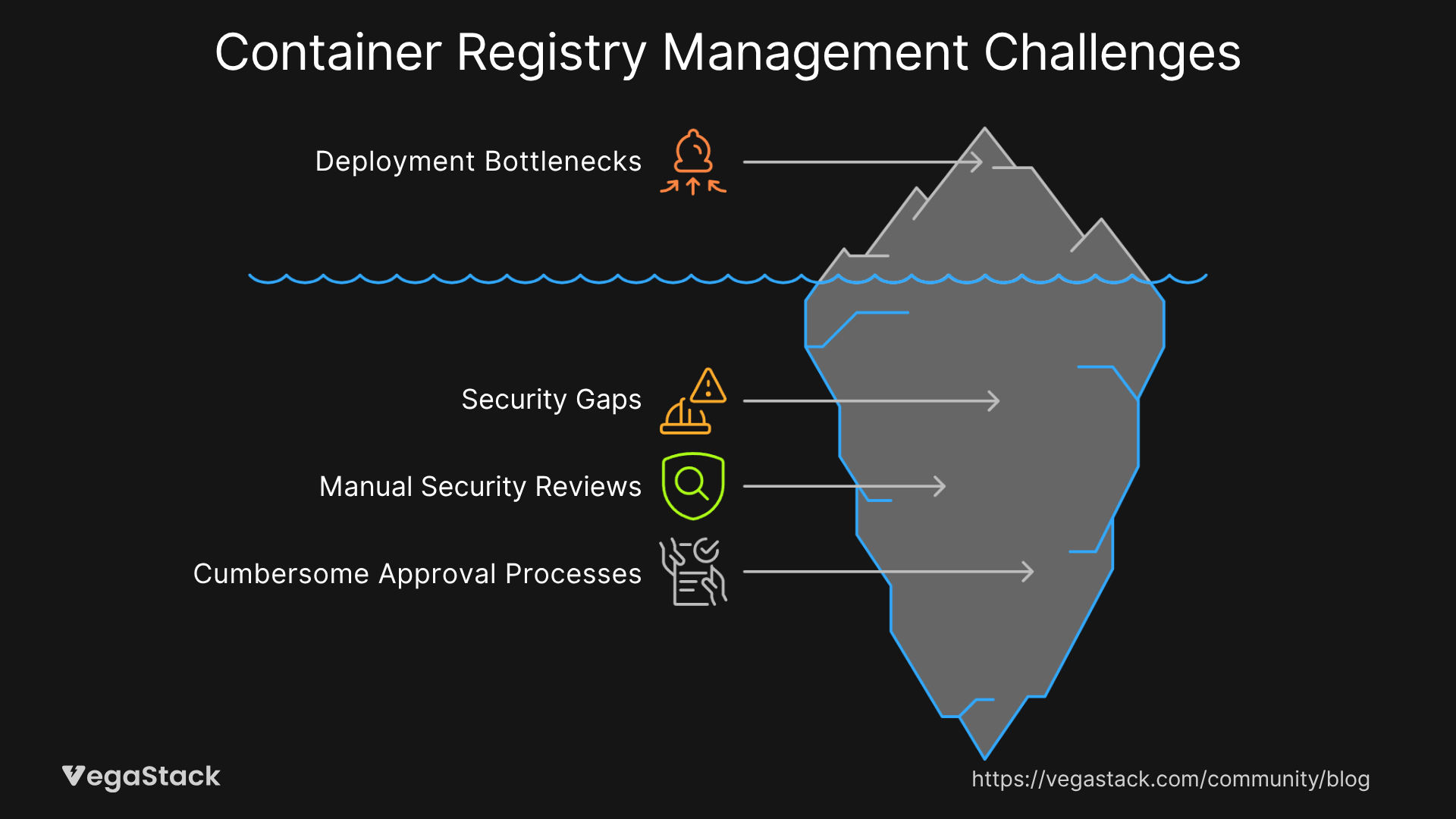
The technical complexities compound rapidly in enterprise environments. Image vulnerability management becomes exponentially more difficult as the number of base images, application layers, and deployment targets increases. Traditional registry solutions often lack the sophisticated policy engines needed to automatically enforce security standards while maintaining development velocity.
Furthermore, image distribution performance issues frequently emerge as teams scale. Slow image pulls can add 10-15 minutes to each deployment cycle, creating significant delays when multiplied across hundreds of daily deployments. Without proper optimization strategies, these performance bottlenecks become major impediments to achieving continuous delivery objectives.
Comprehensive Container Registry Management Framework
Step 1: Implement Multi-Layered Security Scanning
The foundation of effective container registry management begins with comprehensive security scanning that operates at multiple levels. We implement vulnerability scanning that examines both operating system packages and application dependencies, creating a complete security profile for each image. This approach involves integrating scanning tools directly into the registry workflow, ensuring every pushed image undergoes automatic security assessment before becoming available for deployment.
Our scanning strategy includes both static analysis and dynamic vulnerability detection. Static analysis examines image layers for known vulnerabilities, outdated packages, and configuration issues. Dynamic scanning goes deeper, analyzing runtime behavior patterns and identifying potential security risks that static analysis might miss. This dual approach provides comprehensive coverage while minimizing false positives that can slow development workflows.
Step 2: Establish Automated Vulnerability Management Policies
Effective vulnerability management requires automated policy enforcement that balances security requirements with development velocity. We design policy frameworks that automatically categorize vulnerabilities by severity and impact, triggering appropriate responses based on predefined risk thresholds. Critical vulnerabilities block image promotion to production environments, while lower-severity issues generate alerts and remediation recommendations.
The policy engine we implement supports flexible rule configurations that adapt to different application risk profiles. High-security applications might require zero critical vulnerabilities before deployment, while development environments might allow controlled exceptions with appropriate approval workflows. This graduated approach ensures security standards remain enforced without creating unnecessary development friction.
Step 3: Design Intelligent Image Lifecycle Management
Image lifecycle policies form the operational backbone of sustainable registry management. We implement automated policies that manage image retention, promotion workflows, and cleanup processes based on usage patterns and business requirements. These policies prevent registry bloat while ensuring critical images remain available when needed.
Our lifecycle management approach includes automated tagging strategies that track image provenance, testing status, and deployment history. Images progress through defined stages from development to production, with each transition governed by automated quality gates and approval workflows. This systematic approach reduces manual overhead while maintaining deployment quality and traceability.
Step 4: Optimize Distribution Performance
Registry performance optimization requires strategic attention to image architecture, caching strategies, and network distribution patterns. We implement multi-tier caching architectures that position frequently accessed images closer to deployment targets, reducing pull times and network overhead. This includes both registry-level caching and edge distribution strategies that account for geographic distribution of development teams.
Layer optimization becomes crucial for performance at scale. We guide teams in implementing image building best practices that maximize layer reuse and minimize image sizes. This includes strategic placement of frequently changing components in upper layers while keeping stable dependencies in lower, cacheable layers.
Step 5: Implement Access Control and Compliance Framework
Enterprise container registry management requires sophisticated access control mechanisms that integrate with existing identity management systems while supporting fine-grained permissions. We implement role-based access control (RBAC) frameworks that align with organizational structure and compliance requirements, ensuring appropriate separation of duties between development, security, and operations teams.
Compliance management involves implementing audit trails, access logging, and automated reporting mechanisms that support regulatory requirements. This includes tracking who accessed which images, when deployments occurred, and maintaining immutable records of all registry activities for security and compliance auditing.
Step 6: Establish Monitoring and Alerting Systems
Comprehensive monitoring provides visibility into registry performance, security status, and operational health. We implement monitoring solutions that track key metrics including image pull performance, vulnerability scan results, policy violations, and storage utilization. These metrics provide actionable insights for continuous optimization while enabling proactive issue resolution.
Alerting systems we design focus on actionable notifications that enable rapid response to security threats or performance degradation. This includes integration with existing incident management systems and escalation procedures that ensure appropriate team members receive timely notifications about critical issues.
Step 7: Create Disaster Recovery and High Availability Architecture
Enterprise registry management requires robust disaster recovery and high availability strategies that ensure continuous service availability. We implement registry replication strategies that maintain synchronized copies across multiple regions or data centers, enabling rapid failover during outages or disasters. This includes both real-time replication for critical images and scheduled synchronization for less frequently accessed content.
Implementation: Security Scanning Integration
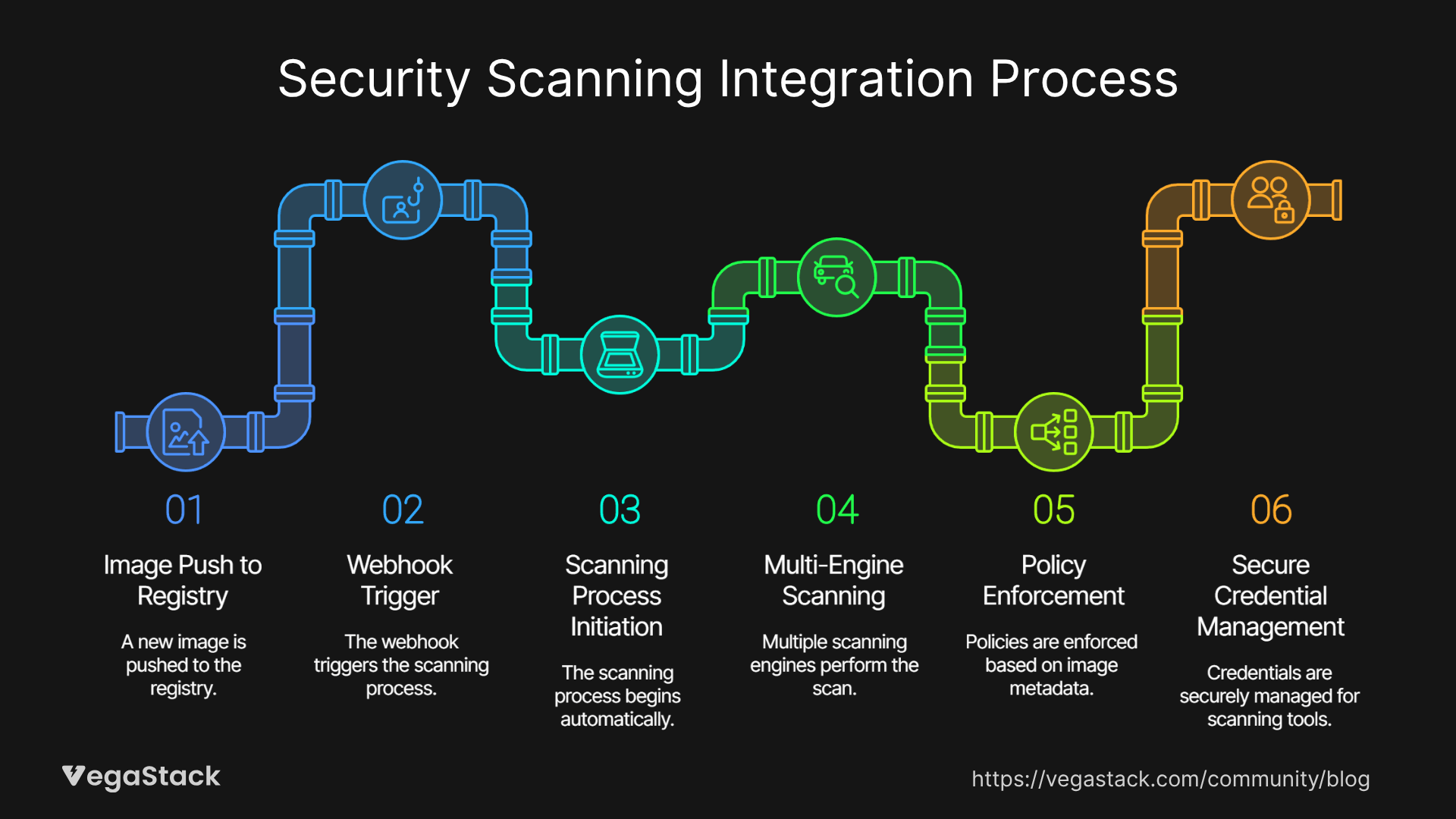
The technical implementation of comprehensive security scanning requires careful integration between registry systems, scanning engines, and development workflows. We typically implement webhook-based architectures that trigger scanning processes automatically when new images are pushed to the registry. This ensures every image receives security assessment without requiring manual intervention or workflow changes from development teams.
The scanning integration we design supports multiple scanning engines simultaneously, providing comprehensive coverage across different vulnerability databases and detection methodologies. This multi-engine approach improves detection accuracy while reducing the risk of missing critical vulnerabilities that might only appear in specific security databases.
Policy enforcement integration becomes particularly complex in enterprise environments with diverse application portfolios and varying security requirements. We implement policy engines that support conditional logic, allowing different scanning thresholds and response actions based on image metadata, target environments, and application classification. This flexibility ensures security policies can adapt to diverse organizational needs without creating unnecessary development friction.
Registry integration also involves implementing secure credential management for scanning tools, ensuring scanning processes can access private registries without exposing authentication credentials. This includes integration with enterprise secret management systems and implementation of least-privilege access principles for scanning infrastructure.
Results and Validation
Our comprehensive container registry management implementations typically deliver significant measurable improvements across multiple operational dimensions. Organizations commonly experience 35-40% reduction in deployment cycle times, primarily due to faster image distribution and automated security approval workflows. This translates to savings of approximately $4,000-$8,000 monthly in developer productivity improvements alone.
Security posture improvements prove equally significant. Clients typically see 80-90% reduction in production security incidents related to vulnerable container images, with automated scanning catching critical vulnerabilities before deployment. One recent client avoided an estimated $12,000 in potential breach remediation costs by catching a critical vulnerability through automated scanning that their previous manual processes had missed.
Performance optimization results include 60-70% improvement in average image pull times, with some organizations seeing even greater improvements for frequently accessed images. Registry storage optimization typically reduces storage costs by 25-35% through intelligent lifecycle management and layer deduplication strategies.
However, we've learned that implementation success depends heavily on organizational change management and team adoption. Technical solutions alone aren't sufficient; successful implementations require comprehensive training programs and gradual workflow transitions that allow teams to adapt to new processes while maintaining productivity.
Key Learnings and Best Practices
Start with Security Foundation First: Organizations achieve better long-term outcomes when they prioritize security scanning and vulnerability management before optimizing for performance or convenience. Retrofitting security into existing workflows proves significantly more difficult than building security-first architectures from the beginning.
Implement Gradual Policy Enforcement: Successful registry management implementations use phased approaches that gradually tighten security policies over time. Immediate enforcement of strict policies often creates development friction that leads to workaround behaviors and reduced security compliance.
Prioritize Developer Experience: Registry management solutions that create friction for developers often fail despite technical excellence. The most successful implementations focus on seamless integration with existing development workflows while providing clear value propositions for development teams.
Invest in Comprehensive Monitoring: Organizations that implement robust monitoring and alerting from the beginning achieve significantly better operational outcomes. Monitoring provides the visibility needed for continuous optimization and rapid issue resolution.
Plan for Scale from Day One: Registry architectures that work well for small teams often fail catastrophically as organizations scale. Designing for enterprise scale requirements from the beginning, even if initially over-provisioned, proves more cost-effective than major architectural changes later.
Automate Ruthlessly: Manual processes in registry management become operational bottlenecks that limit scalability and introduce human error risks. Successful implementations automate not just scanning and deployment processes, but also policy management, reporting, and compliance activities.
Conclusion
Effective container registry management transforms from operational overhead into strategic advantage when implemented with comprehensive security, optimization, and lifecycle management strategies. Organizations that invest in proper registry management see substantial improvements in deployment velocity, security posture, and operational efficiency while reducing long-term maintenance overhead.
The key to success lies in implementing systematic approaches that address security, performance, and operational requirements simultaneously rather than treating them as separate concerns. When properly executed, container registry management becomes an enabler of rapid, secure software delivery that supports enterprise-scale development objectives.




