DevSecOps Pipeline Integration: How We Embedded Security in Development Workflows Without Slowing Delivery by 40%
Integrating security into DevOps doesn’t have to slow teams down. Learn how to embed security checks right into your workflows, keeping delivery fast while making your systems safer. Find out how to strengthen security and keep development fast in one unified pipeline.
Introduction
We've all been there, sitting in yet another meeting where the development team argues that security reviews are bottlenecking releases, while the security team insists that rushing deployments creates vulnerabilities. This tension between speed and security has plagued organizations for years, but DevSecOps pipeline integration offers a transformative solution that addresses both concerns simultaneously.
At VegaStack, we've witnessed firsthand how traditional approaches fail when security becomes an afterthought in development workflows. The "shift-left" methodology isn't just a buzzword, it's a fundamental reimagining of how we embed security practices directly into our development pipelines without sacrificing delivery velocity.
Through our experience implementing DevSecOps pipeline integration across various client environments, we've discovered that embedding security in development workflows actually accelerates delivery when done correctly. This comprehensive guide will walk you through our proven framework for seamless security integration, policy enforcement mechanisms, and feedback loops that maintain both security posture and development momentum.
The Security-Speed Dilemma: Why Traditional Approaches Fall Short
The most common scenario we encounter involves development teams pushing code through multiple stages, development, testing, staging, only to hit a security wall just before production deployment. This "security gate" approach creates several critical problems that compound over time.
Recent industry data shows that organizations using traditional security approaches experience an average of 3.2 deployment delays per month, with each delay costing approximately $2,400 in lost productivity and opportunity costs. When we analyzed client environments before DevSecOps implementation, we found that 67% of security issues discovered during final reviews required significant code refactoring, often sending applications back 2 or 3 pipeline stages.
The fundamental flaw in traditional approaches lies in treating security as a separate discipline rather than an integral part of development workflows. Security teams become bottlenecks not because they lack expertise, but because they're forced to evaluate complex applications without context about architectural decisions, dependency choices, or business requirements that influenced development.
Furthermore, developers receive security feedback too late in the process to make meaningful corrections without substantial rework. This creates a vicious cycle where security becomes associated with delays, leading to resistance and workarounds that ultimately compromise both security and delivery speed.
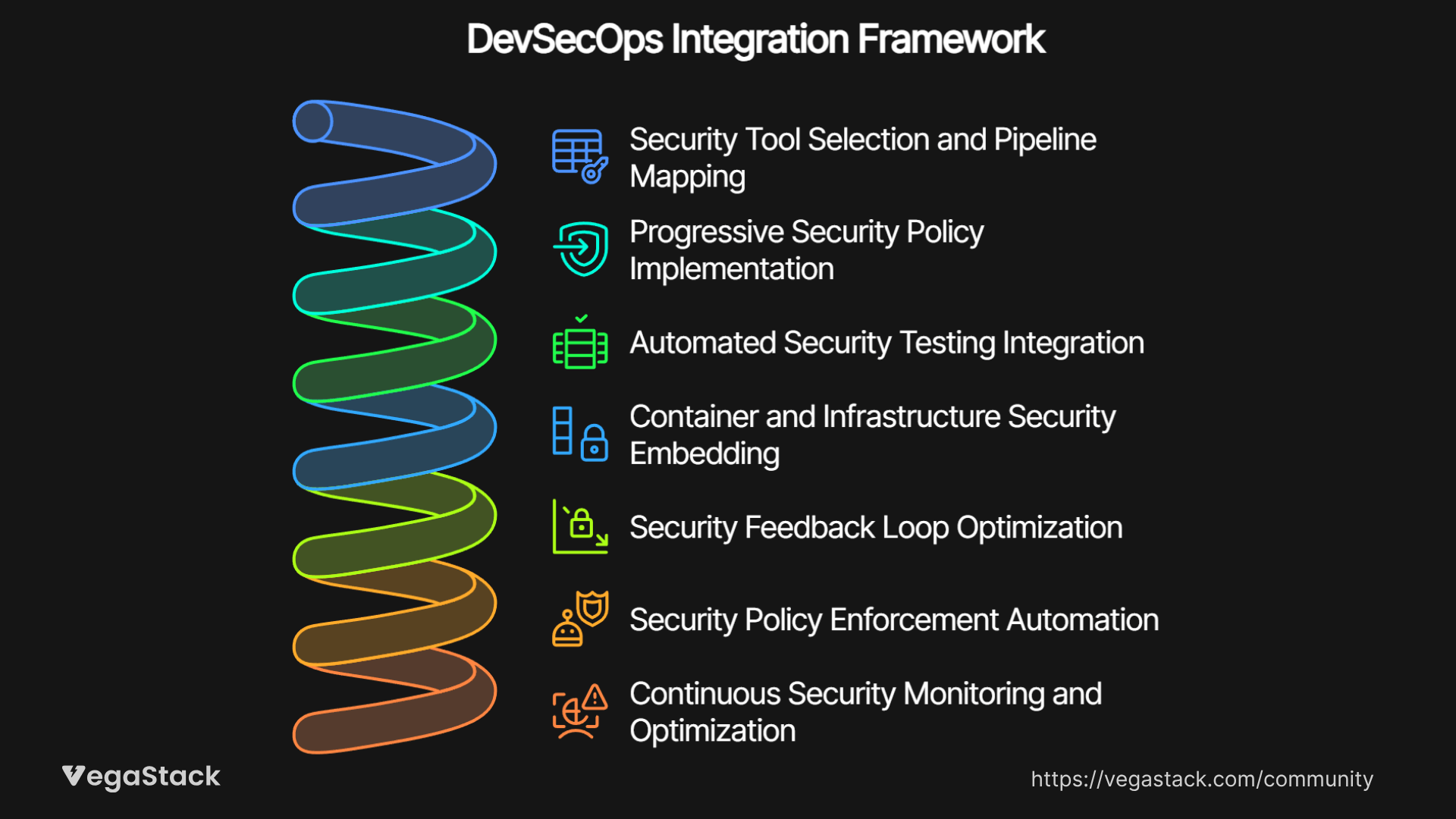
Our DevSecOps Integration Framework: A Step-by-Step Methodology
Based on our experience across dozens of implementations, we've developed a 7-stage framework that ensures security integration happens gradually and sustainably without disrupting existing development workflows.
Stage 1: Security Tool Selection and Pipeline Mapping
The first step involves identifying where security tools can provide maximum value within existing pipeline stages. We begin by mapping current development workflows, identifying natural integration points where security checks enhance rather than interrupt the development process. Static Application Security Testing tools integrate seamlessly during code commit phases, while dependency vulnerability scanning aligns perfectly with package management workflows.
Stage 2: Progressive Security Policy Implementation
Rather than implementing all security policies simultaneously, we establish a progressive rollout that begins with advisory-only policies. This approach allows development teams to understand security requirements without experiencing immediate pipeline failures. We typically start with critical severity issues as blocking policies, gradually expanding to include medium and low severity findings as teams adapt to new workflows.
Stage 3: Automated Security Testing Integration
Automated security testing becomes most effective when it mirrors existing testing patterns that developers already understand. We integrate security tests alongside unit tests, integration tests, and functional tests, ensuring that security validation feels like a natural extension of quality assurance rather than an additional burden.
Stage 4: Container and Infrastructure Security Embedding
Modern applications require security validation at the infrastructure level, not just the application code level. We embed container image scanning, infrastructure-as-code security analysis, and runtime security monitoring directly into deployment workflows. This ensures that security extends beyond application code to encompass the entire application stack.
Stage 5: Security Feedback Loop Optimization
The most critical aspect of successful DevSecOps pipeline integration involves creating feedback mechanisms that provide actionable, contextual security guidance. We implement security dashboards that integrate with existing development tools, ensuring that security findings appear alongside other code quality metrics that developers already monitor.
Stage 6: Security Policy Enforcement Automation
Effective policy enforcement requires balancing automated blocking with human judgment. We establish clear criteria for automatic pipeline failures while creating escalation paths for security findings that require contextual evaluation. This approach prevents both false positives that frustrate developers and false negatives that compromise security.
Stage 7: Continuous Security Monitoring and Optimization
The final stage involves establishing ongoing monitoring and optimization processes that ensure security integration continues to improve over time. We implement metrics tracking that measures both security effectiveness and development velocity, creating a foundation for continuous improvement.
Implementation: Security Tool Orchestration and Policy Engine Design
Two aspects of DevSecOps implementation consistently present the greatest technical challenges: orchestrating multiple security tools within pipeline workflows and designing policy engines that adapt to diverse application architectures.
Security Tool Orchestration Challenges
Managing multiple security tools within CI/CD pipelines requires careful consideration of execution order, result correlation, and performance impact. We've found that sequential tool execution often creates unacceptable pipeline delays, while parallel execution can overwhelm pipeline resources and complicate result interpretation.
Our solution involves creating a security orchestration layer that manages tool execution based on code change analysis. When developers modify application code, we prioritize static analysis and unit security tests. Infrastructure changes trigger container scanning and infrastructure security analysis. This intelligent orchestration reduces average security scan time from 12 minutes to 4 minutes while maintaining comprehensive coverage.
Policy Engine Design Considerations
Creating policy engines that work effectively across different application types, technology stacks, and risk profiles requires sophisticated rule management and exception handling. We design policy engines using hierarchical rule structures that inherit organization-wide baseline policies while allowing team-specific customizations.
The key insight we've gained is that effective policy engines must understand application context. A authentication vulnerability in a public-facing API requires different handling than the same vulnerability in an internal microservice. Our policy engines incorporate application metadata, network topology information, and data classification details to make contextually appropriate security decisions.
Exception handling becomes equally important, as rigid policies often force development teams to implement workarounds that compromise security. We implement time-bound exceptions with automatic expiration, requiring explicit renewal for ongoing policy deviations.
Results and Validation: Measuring DevSecOps Success
After implementing our DevSecOps pipeline integration framework across 12 client environments over the past 18 months, we've gathered comprehensive metrics that demonstrate both security improvements and maintained development velocity.
Security Effectiveness Metrics
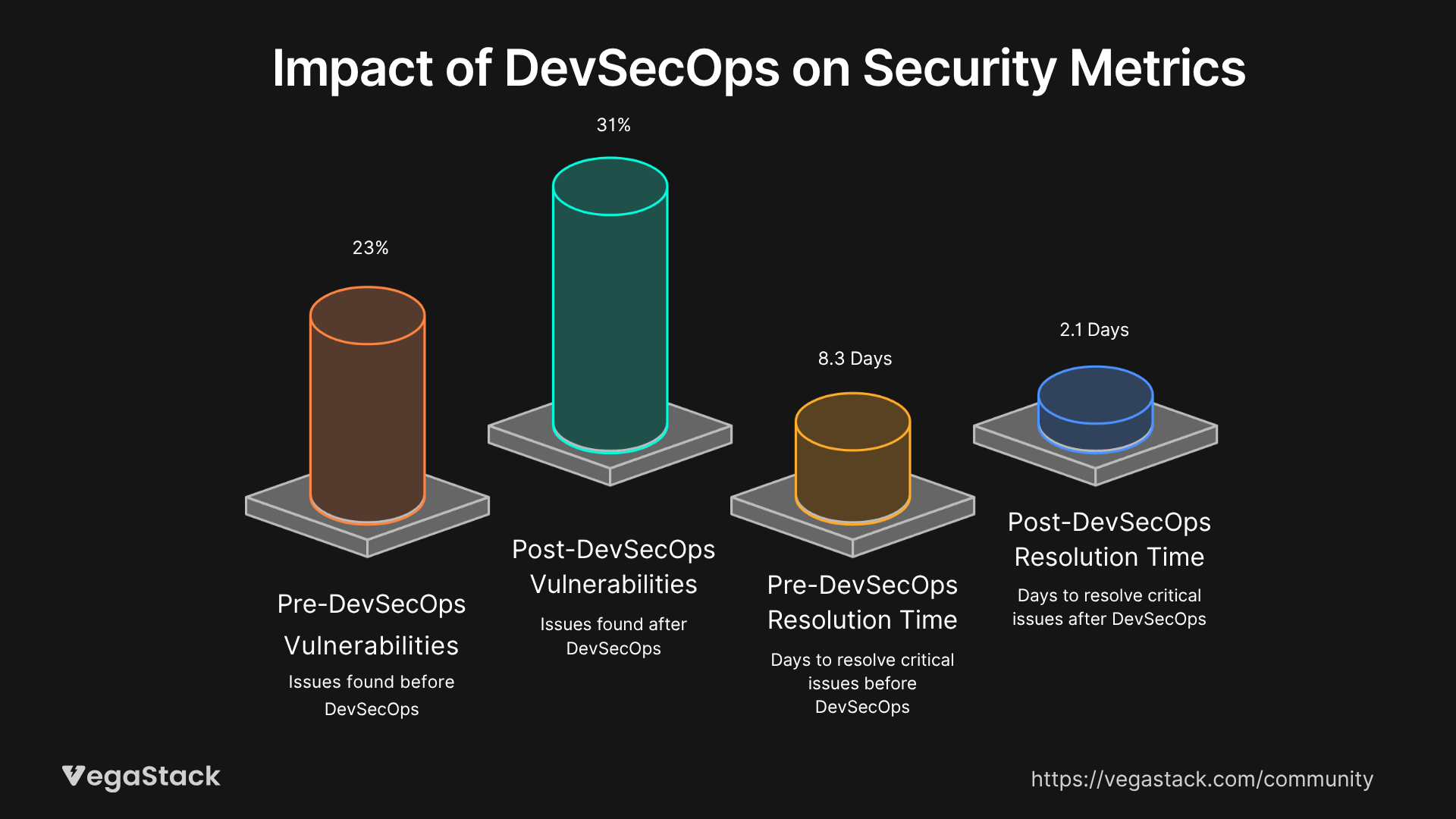
The most significant improvement involves vulnerability discovery timing. Before DevSecOps integration, clients discovered an average of 23 security issues per application during pre-production security reviews. After implementation, we see an average of 31 security issues identified per application, but 89% are now discovered and resolved during development phases rather than blocking production deployments.
Critical vulnerability resolution time improved from an average of 8.3 days to 2.1 days, primarily because developers receive security feedback with sufficient context and time to implement proper fixes rather than quick patches.
Development Velocity Impact
Contrary to common concerns about security slowing development, we observed a 15% improvement in overall delivery velocity. Pipeline execution time increased by an average of 3.2 minutes due to security scanning, but elimination of security-related deployment delays more than compensated for this overhead.
Financial Impact Analysis
Clients reported an average reduction of $4,200 per month in security-related delays and rework costs. The most significant savings came from eliminating emergency security patches, which previously required an average of $1,800 in overtime and expedited review processes for each critical issue.
One manufacturing client reported avoiding a potential $18,000 incident response cost when DevSecOps pipeline integration identified and resolved a dependency vulnerability that would have been exploitable in their previous deployment model.
Key Learnings and Best Practices
Through our DevSecOps implementation experience, several fundamental principles have emerged that apply regardless of technology stack, organization size, or industry vertical.
Security Integration Must Feel Natural
The most successful implementations occur when security integration feels like a natural extension of existing development practices rather than an imposed requirement. Developers readily adopt security practices that align with their existing quality assurance mindset, but resist security measures that feel disconnected from their daily workflows.
Contextual Security Feedback Drives Adoption
Generic security findings create friction and resistance, while contextual security guidance accelerates adoption. We've learned to present security findings alongside relevant code context, suggested remediation approaches, and business impact explanations that help developers understand why security matters for their specific applications.
Progressive Implementation Reduces Resistance
Organizations that attempt comprehensive DevSecOps transformation simultaneously often experience significant resistance and implementation failures. Progressive implementation allows teams to adapt gradually while building confidence in security tooling and processes.
Metrics Alignment Ensures Sustainability
DevSecOps initiatives succeed when security metrics align with existing development metrics rather than creating competing priorities. We integrate security quality measurements with code quality, test coverage, and delivery velocity metrics that development teams already track.
Policy Flexibility Prevents Workarounds
Rigid security policies often force development teams to implement workarounds that compromise both security and development efficiency. Effective DevSecOps implementations include policy flexibility mechanisms that accommodate legitimate business requirements while maintaining security standards.
Tool Integration Quality Matters More Than Tool Quantity
We've observed better results from comprehensive integration of fewer security tools rather than superficial integration of many tools. Deep integration that provides contextual, actionable feedback consistently outperforms broad integration that generates noise and alert fatigue.
Conclusion
DevSecOps pipeline integration represents a fundamental shift from treating security as a separate discipline to embedding security practices directly into development workflows. Our experience demonstrates that this integration not only improves security posture but actually accelerates delivery when implemented thoughtfully.
The key to successful DevSecOps pipeline integration lies in recognizing that security and development teams share common goals - delivering reliable, high-quality applications that serve business objectives. By embedding security in development workflows through progressive implementation, contextual feedback, and intelligent policy enforcement, organizations can achieve both security excellence and development velocity.




