How to Configure SSH Keys on Ubuntu 24.04
Configure SSH Keys on Ubuntu 24.04 with our step-by-step tutorial. SSH keys are cryptographic pairs for secure computer communication.

Introduction
Before we begin talking about how to configure SSH Keys on Ubuntu 24.04, let's briefly understand – What is SSH Keys?
SSH keys, short for Secure Shell keys, are a pair of cryptographic keys used to secure communication between two computers. They consist of a public key, which is shared with others, and a private key, which is kept secret. This technology enhances security by ensuring that only the holder of the private key can access the data or system.
SSH keys are vital for secure remote access, file transfers, and authentication processes. When used correctly, they provide a robust method for protecting sensitive information and preventing unauthorized access.
In this tutorial, you will configure SSH Keys on Ubuntu 24.04. We will also address a few FAQs on how to configure SSH Keys on Ubuntu 24.04.
Configure SSH Keys on Ubuntu 24.04
Step 1:
Generate a unique key-pair for each user, allowing them to log in to the SSH Server Host using a common user account and proceed as follows,
ssh-keygen
To List the files and directories in the .ssh directory within the home directory in a detailed format, run the following command,
ll ~/.ssh
Now, appends the contents of the id_ed25519.pub file to the authorized_keys file in the .ssh directory.
cat ~/.ssh/id_ed25519.pub >> ~/.ssh/authorized_keys
Step 2:
Transfer the private key generated on the server to the client, enabling login via key-pair authentication,
Create the .ssh Directory and Set Permissions for the .ssh Directory
mkdir ~/.ssh
chmod 700 ~/.ssh
Transfer the Private Key:
scp [email protected]:/home/ubuntu/.ssh/id_ed25519 ~/.ssh/
Authenticate Using the Private Key:
ssh [email protected]
Output
Enter passphrase for key '/home/ubuntu/.ssh/id_ed25519': # passphrase if you set
Welcome to Ubuntu 24.04 LTS (GNU/Linux 6.8.0-31-generic x86_64)
.....
.....
Step 3:
Setting PasswordAuthentication no enhances security
Open the SSH Configuration File:
vi /etc/ssh/sshd_config
Modify the Configuration:
Find the line that contains PasswordAuthentication and change its value to no. Uncomment the line if it's commented out.
PasswordAuthentication no
Line 62: Ensure that the following setting is present and set to no.
KbdInteractiveAuthentication no
Check for Additional Configuration Files:
cat /etc/ssh/sshd_config.d/50-cloud-init.conf
This command displays the contents of an additional configuration file, 50-cloud-init.conf, located in the sshd_config.d directory.
If this file contains:
PasswordAuthentication yes
It means that this file overrides the settings in sshd_config by allowing password authentication.
Remove the Additional Configuration File:
rm /etc/ssh/sshd_config.d/50-cloud-init.conf
This command deletes the 50-cloud-init.conf file to ensure that the settings in sshd_config are not overridden.
Restart the SSH
systemctl restart ssh
SSH Key-Pair Authentication on Windows Client #1
Here’s an example of logging into an SSH server from a Windows client using PuTTY. Before doing so, make sure to transfer the private key to the Windows client computer.
Launch Puttygen.exe, which is included with PuTTY (found in the same folder as Putty.exe). If it’s not included, download it from the official site (www.chiark.greenend.org.uk/~sgtatham/putty/). Once Puttygen.exe is open, click the Load button in the window that appears.
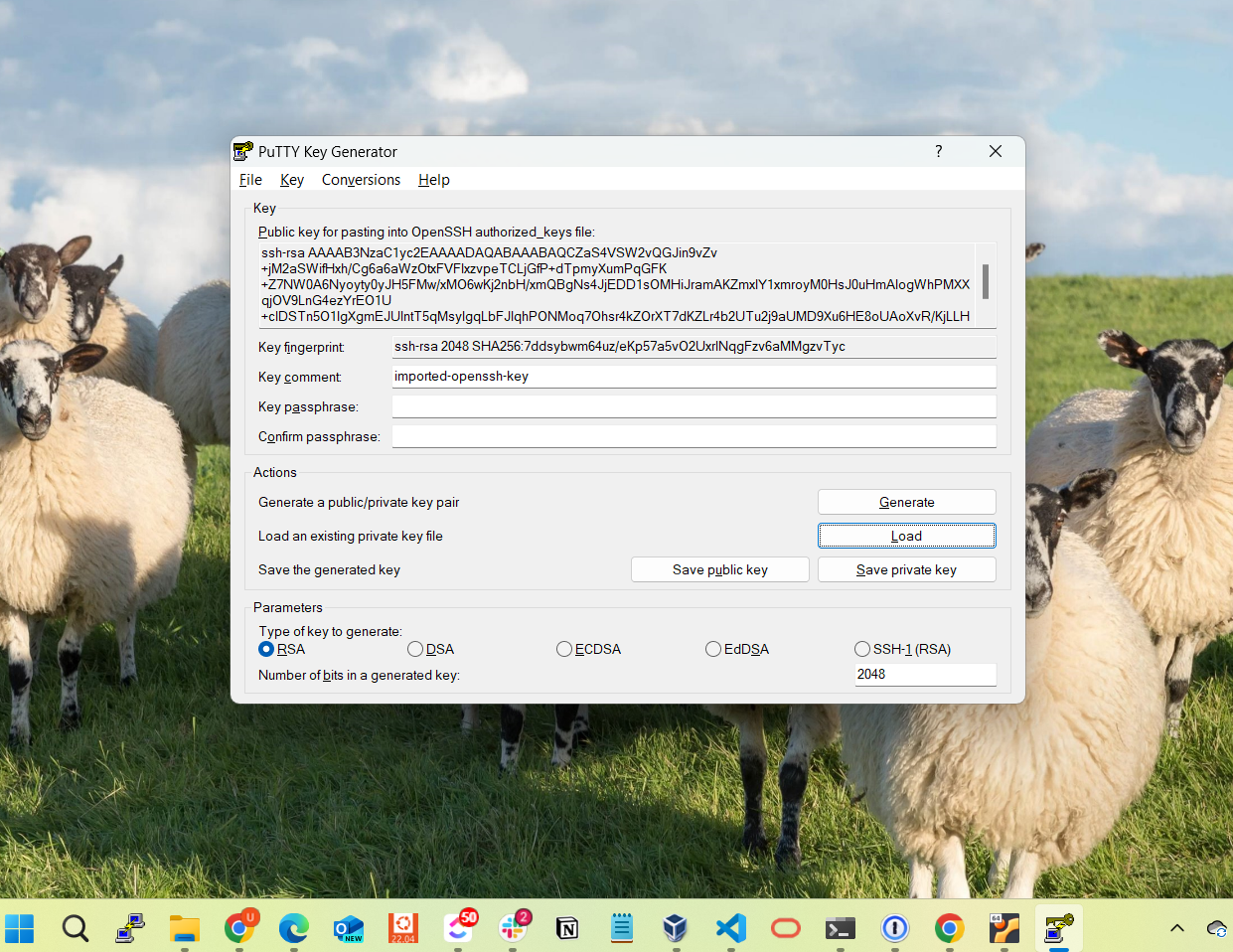
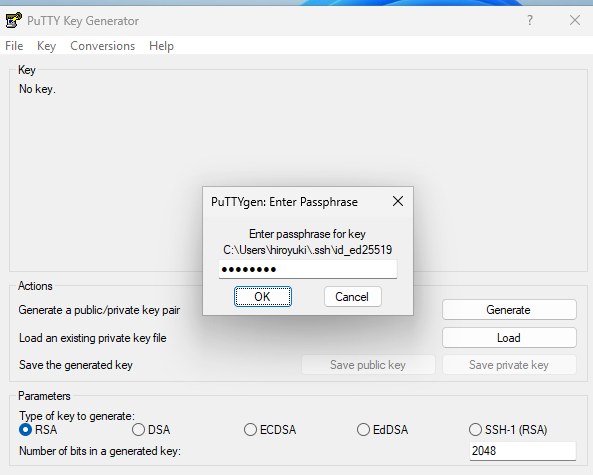
Select the private key you transferred from the SSH server. If the key is protected by a passphrase, you will be prompted to enter it. If no passphrase is set, this step will be skipped.
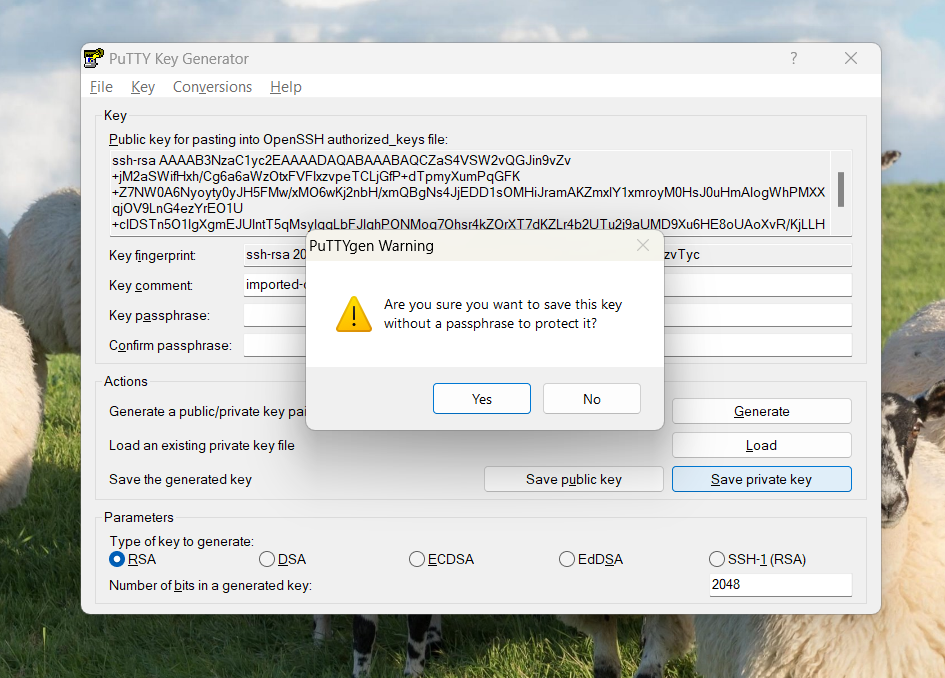
Click the Save private key button to save the key to a folder of your choice with any file name you prefer.
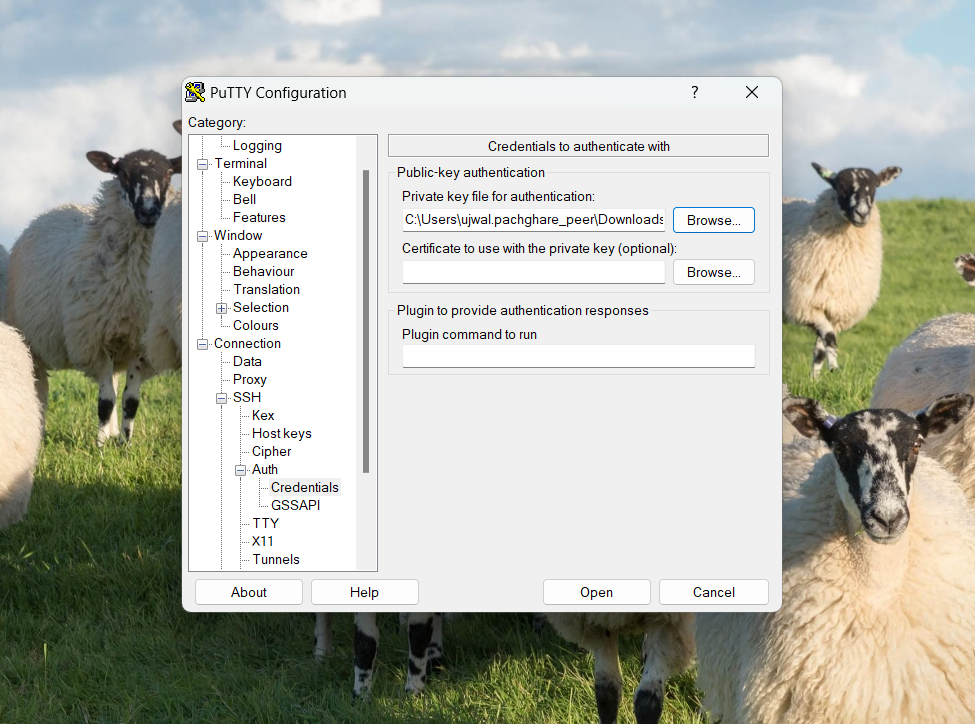
Open PuTTY and navigate to Connection - SSH - Auth - Credentials on the left pane. Then, specify your private key in the Private key file field.
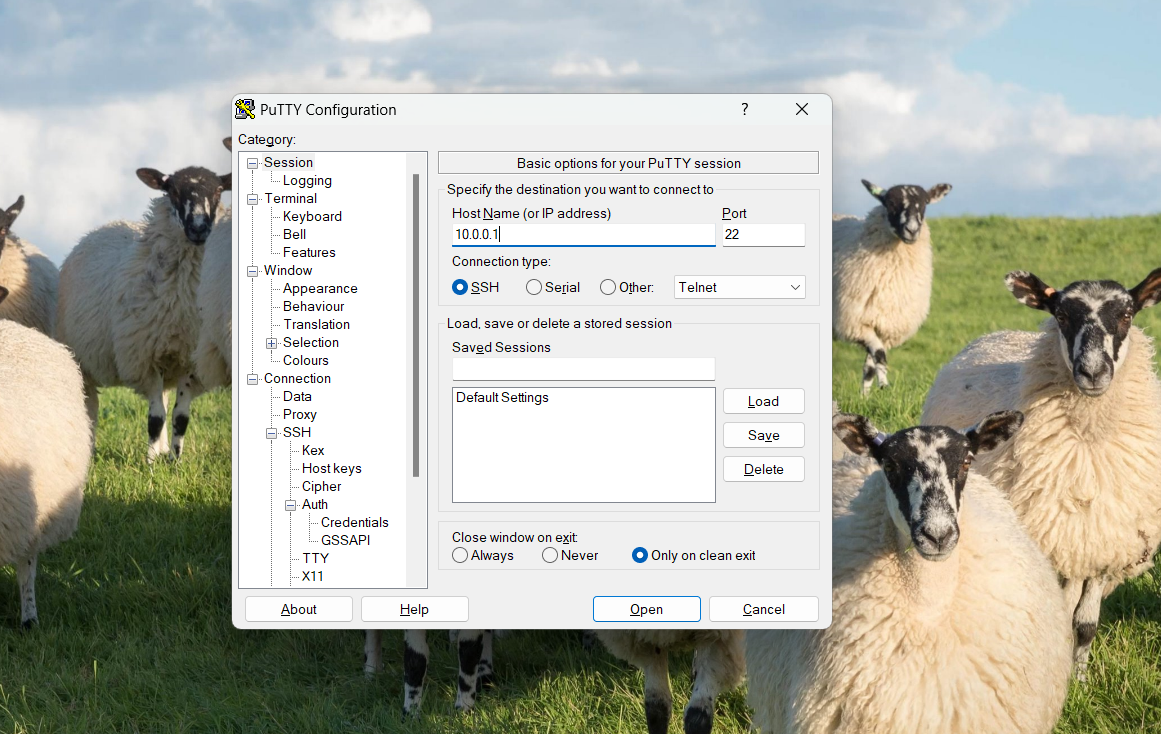
Return to the Session section on the left pane and enter your SSH server host to establish the connection.
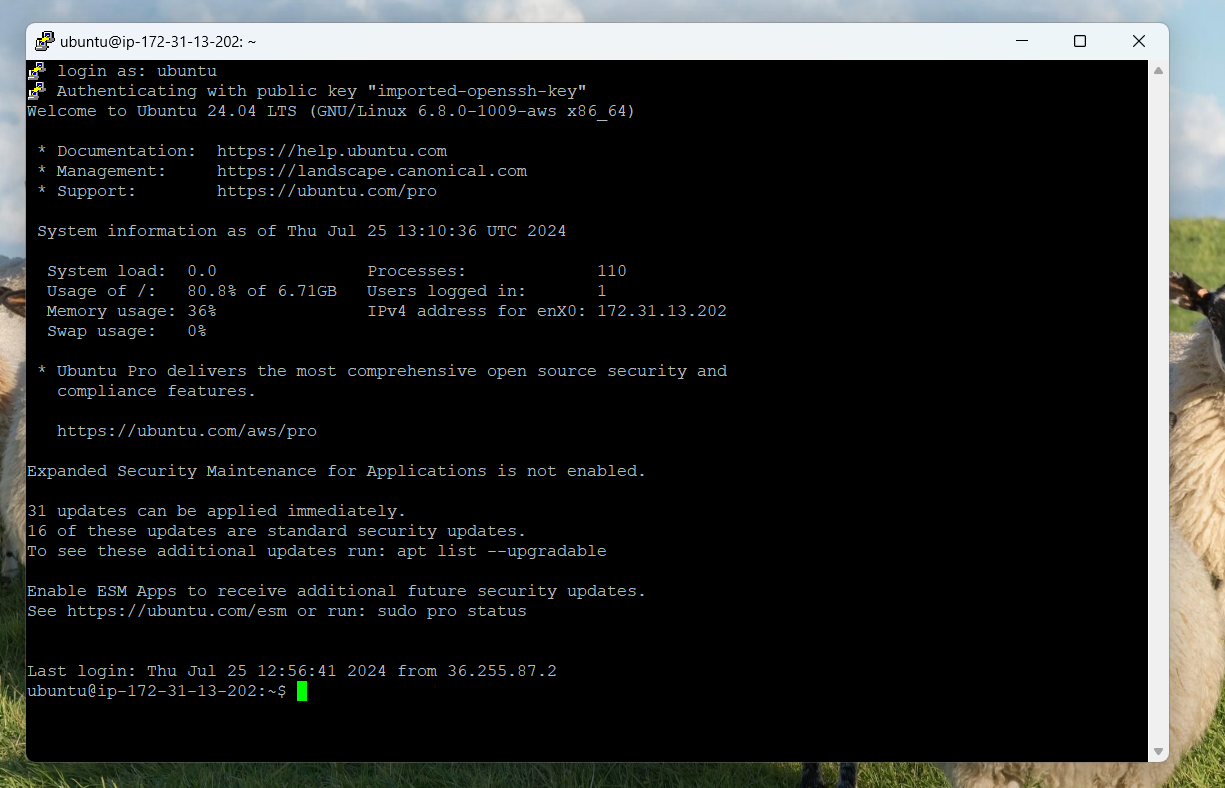
When using an SSH key-pair, you will be prompted for the passphrase if one is set. Enter the passphrase to proceed.
SSH Key-Pair Authentication on Windows #2
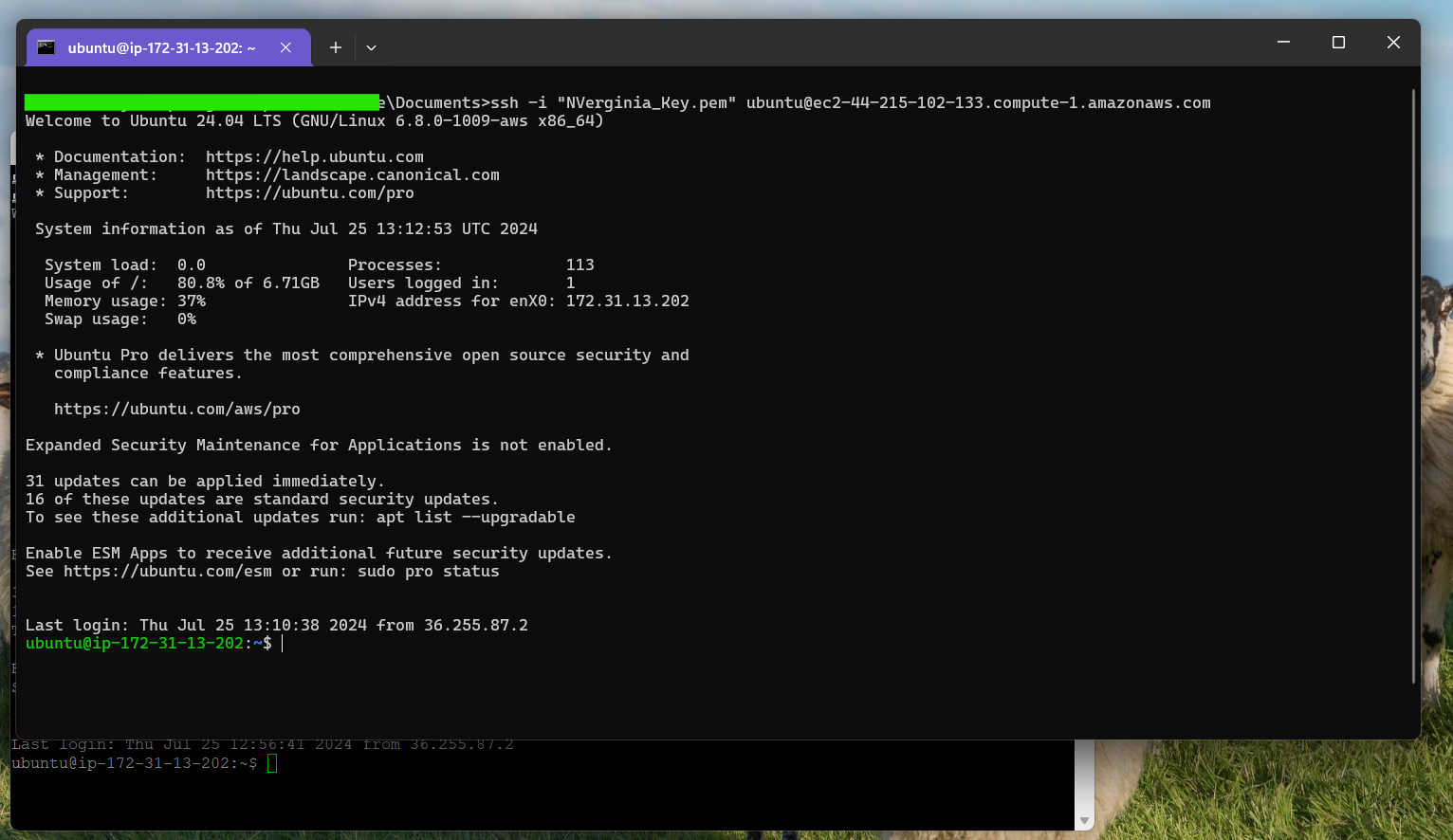
OpenSSH Client is available as a Windows feature, allowing you to authenticate with SSH key-pair without needing PuTTY or other third-party software. Transfer your private key to your Windows machine and place it in the (.ssh) folder within the user’s home directory. Once done, you can use key-pair authentication.
FAQs to Configure SSH Keys on Ubuntu 24.04
Where are the generated keys stored?
By default, the public key is saved as ~/.ssh/id_rsa.pub and the private key is ~/.ssh/id_rsa.
What permissions should the .ssh directory and authorized_keys file have?
The .ssh directory should have permissions 700 and be owned by the user. The authorized_keys file should have permissions 600 and also be owned by the user.
How do I list the keys currently loaded in the agent?
Run ssh-add -l to list the fingerprints of the keys currently loaded in the SSH agent.
How do I remove a key from the SSH agent?
To remove a specific key: ssh-add -d ~/.ssh/id_rsa. To remove all keys: ssh-add -D
Do I need a passphrase for my SSH key?
It's optional, but adding a passphrase enhances security. You will need to enter it whenever you use the key.
How can I change my SSH key passphrase?
Use this command: ssh-keygen -p -f ~/.ssh/id_rsa. Follow the prompts to change it.
What if I lose my private key?
If you lose your private key, you cannot access servers that require it. You will need to generate a new key pair and add the new public key to the servers.
Conclusion
We hope this tutorial helped you understand how to configure SSH Keys on Ubuntu 24.04.
If you have any queries, please leave a comment below, and we’ll be happy to respond to them for sure.