Introduction
Before we begin talking about how to Enable or Disable AppArmor on Ubuntu 22.04, let's briefly understand – What is AppArmor?
AppArmor is a security software for Linux systems that protects applications and processes by limiting their access to specific parts of the system. It creates a security profile for each application, which defines what resources it can access. This helps prevent malicious programs from causing harm. AppArmor is designed to be easy to use and provides an additional layer of defense against cyber threats on Linux systems.
By setting up AppArmor profiles, system administrators can control the permissions of various applications, making it harder for attackers to exploit vulnerabilities. This proactive approach enhances the overall security of the system, ensuring that only authorized actions are allowed. AppArmor is an essential tool for protecting Linux servers and desktops from unauthorized access and potential security breaches.
In this tutorial, you will enable or disable AppArmor on Ubuntu 22.04. We will also address a few FAQs on how to enable or disable AppArmor on Ubuntu 22.04.
Pre-Steps Before Managing Apparmor on Ubuntu 22.04
Install Additional Apparmor Packages
Make sure the apparmor-utils package is installed on your system in order to take full advantage of AppArmor's capabilities. This package is crucial because it offers a number of commands that are required to properly manage AppArmor.
To commence, first open your terminal and run the installation command:
sudo apt install apparmor-utils apparmor-notify apparmor-profiles apparmor-profiles-extra
This command extends the functionality of AppArmor by installing notification support and extra profiles in addition to the standard utilities.
Check AppArmor Status on Ubuntu
On Ubuntu systems, AppArmor is usually pre-installed and activated. To ascertain its present state, employ the command:
Example Output:
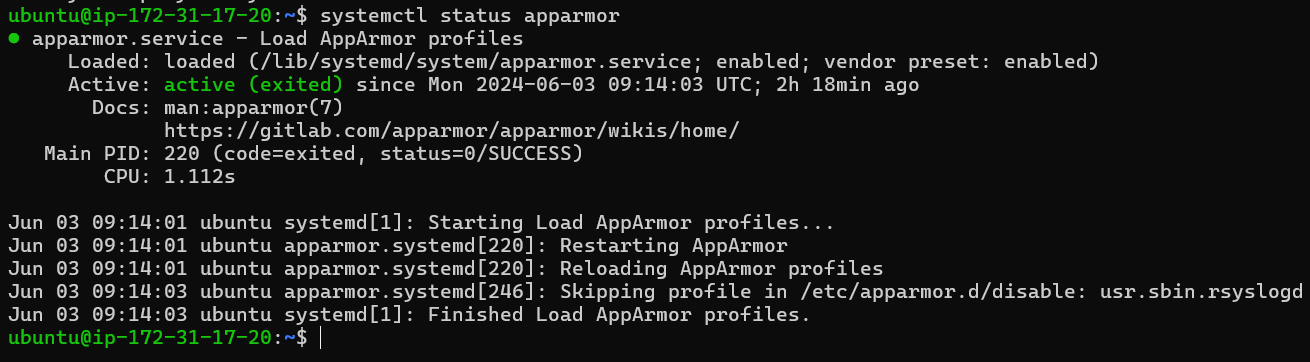
To verify that AppArmor is up and running, use systemctl to check its status. This is an important check because it verifies that AppArmor is currently active on your system. Although there are other ways to verify this, systemctl offers a dependable and simple way to get started.
Managing Systemd Commands for AppArmor
Stopping AppArmor
To terminate the AppArmor service, run:
sudo systemctl stop apparmor
Disabling AppArmor on System Boot
Use the following to stop AppArmor from booting up automatically:
sudo systemctl disable apparmor
Starting AppArmor
Run this to launch the AppArmor service, especially after stopping it:
sudo systemctl start apparmor
Enabling AppArmor on System Boot (Default)
To revert to the default setting where AppArmor starts at boot, execute:
sudo systemctl enable apparmor
Restarting AppArmor
Restart AppArmor to make changes take effect or to reset the service:
sudo systemctl restart apparmor
Reloading AppArmor
Reload AppArmor to apply configuration changes without having to restart the service:
sudo systemctl reload apparmor
Check AppArmor Profiles Loaded on Ubuntu 22.04
Reviewing Current AppArmor Profiles
It's important to check the profiles of AppArmor before making any changes to its settings. The apparmor_status command, which offers a thorough overview of the loaded profiles and their operational modes, is used to accomplish this. Use the terminal to enter the following command:
sudo apparmor_status
The number of loaded profiles, profiles in enforce mode, and any related processes are among the details that are output by this command. The enforce mode displays the active profiles that are presently limiting the behaviors of applications in accordance with their own rules. Before making any changes, it is imperative to comprehend the current security posture by reviewing this overview.
Example Output:
Output
apparmor module is loaded.
63 profiles are loaded.
45 profiles are in enforce mode.
/snap/snapd/17883/usr/lib/snapd/snap-confine
/snap/snapd/17883/usr/lib/snapd/snap-confine//mount-namespace-capture-helper
/snap/snapd/17950/usr/lib/snapd/snap-confine
/snap/snapd/17950/usr/lib/snapd/snap-confine//mount-namespace-capture-helper
/usr/bin/evince
/usr/bin/evince-previewer
/usr/bin/evince-previewer//sanitized_helper
/usr/bin/evince-thumbnailer
/usr/bin/evince//sanitized_helper
/usr/bin/man
/usr/bin/pidgin
/usr/bin/pidgin//sanitized_helper
/usr/bin/totem
/usr/bin/totem-audio-preview
/usr/bin/totem-video-thumbnailer
/usr/bin/totem//sanitized_helper
/usr/lib/NetworkManager/nm-dhcp-client.action
/usr/lib/NetworkManager/nm-dhcp-helper
/usr/lib/connman/scripts/dhclient-script
/usr/lib/snapd/snap-confine
/usr/lib/snapd/snap-confine//mount-namespace-capture-helper
/usr/sbin/cups-browsed
/{,usr/}sbin/dhclient
apt-cacher-ng
lsb_release
man_filter
man_groff
nvidia_modprobe
nvidia_modprobe//kmod
snap-update-ns.firefox
snap-update-ns.snap-store
snap-update-ns.snapd-desktop-integration
snap.firefox.firefox
snap.firefox.geckodriver
snap.firefox.hook.configure
snap.firefox.hook.connect-plug-host-hunspell
snap.firefox.hook.disconnect-plug-host-hunspell
snap.firefox.hook.post-refresh
snap.snap-store.hook.configure
snap.snap-store.snap-store
snap.snap-store.ubuntu-software
snap.snap-store.ubuntu-software-local-file
snap.snapd-desktop-integration.hook.configure
snap.snapd-desktop-integration.snapd-desktop-integration
tcpdump
18 profiles are in complain mode.
/usr/bin/irssi
avahi-daemon
dnsmasq
dnsmasq//libvirt_leaseshelper
identd
klogd
mdnsd
nmbd
nscd
php-fpm
ping
samba-bgqd
smbd
smbldap-useradd
smbldap-useradd///etc/init.d/nscd
syslog-ng
syslogd
traceroute
0 profiles are in kill mode.
0 profiles are in unconfined mode.
3 processes have profiles defined.
3 processes are in enforce mode.
/usr/sbin/cups-browsed (1025)
/snap/snapd-desktop-integration/49/usr/bin/snapd-desktop-integration (1632) snap.snapd-desktop-integration.snapd-desktop-integration
/snap/snapd-desktop-integration/49/usr/bin/snapd-desktop-integration (1717) snap.snapd-desktop-integration.snapd-desktop-integration
0 processes are in complain mode.
0 processes are unconfined but have a profile defined.
0 processes are in mixed mode.
0 processes are in kill mode.
The loaded profiles will be displayed in detail in the output, indicating which are actively enforcing security policies and which are in a more lenient complain mode. For example, you may see profiles for apps like snapd or network services like dnsmasq. For system administrators looking to maintain or improve security measures, this visibility is essential.
Alternative Status Check: Using aa-status
Using the aa-status command is an additional way to verify AppArmor profiles. This provides a closer look at the profiles:
sudo aa-status
This command lists all profiles and their statuses, including those in enforced, complain, and unconfined modes; it functions similarly to apparmor_status. Comprehending these modes is crucial for troubleshooting and optimizing the functionality of AppArmor.
Backing Up AppArmor Profiles
Making a backup of AppArmor's profiles is a suggested best practice before making any changes to it. This guarantees that, in case of emergency, you can return to a known configuration. Run the subsequent command to create a backup of the profiles:
sudo cp -R /etc/apparmor.d /etc/apparmor.d.bak
This command protects your original configuration by copying the current AppArmor profiles to a backup directory, /etc/apparmor.d.bak. Having this backup gives you a safety net so you can play around with or adjust AppArmor settings without worrying about losing your initial setup.
How to Disable AppArmor Profile on Ubuntu 22.04
Navigating to the AppArmor Profiles Directory
To start, navigate to the directory containing the AppArmor profiles. To accomplish this, navigate to /etc/apparmor.d:
cd /etc/apparmor.d
Listing Available AppArmor Profiles
Then, make a list of all the profiles in this directory to find the one you want to disable:
ls -s
All the profiles kept in the /etc/apparmor.d directory are shown by this command. You can choose the exact profile you want to disable from this list.
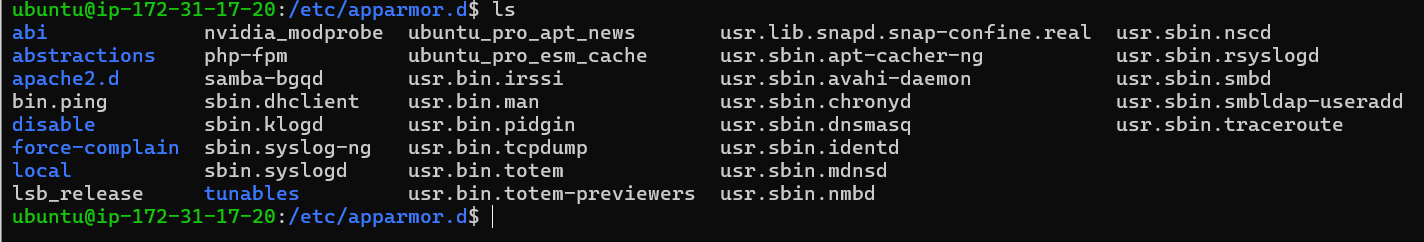
Disabling a Specific AppArmor Profile
The aa-disable command can be used to disable a selected profile. This enables you to disable specific profiles without affecting AppArmor's overall functionality. To disable the usr.sbin.cupsd profile, for example:
sudo aa-disable /etc/apparmor.d/<profile-name>
Example of Command Execution
By running this command, the usr.sbin.cupsd profile will be disabled. This quick action keeps AppArmor's protection for other apps intact, while enabling you to promptly handle any problems brought on by this particular profile.
sudo aa-disable /etc/apparmor.d/usr.sbin.cupsd
Example Output:
Output
Disabling /etc/apparmor.d/usr.sbin.cupsd
Viewing Disabled AppArmor Profiles
Once a profile has been disabled, you can check the /etc/apparmor.d/disable directory to see which profiles are disabled at the moment:
ls /etc/apparmor.d/disable

A list of all the profiles in AppArmor that are currently disabled is provided by this command. It's a helpful tool for keeping track of and managing the profiles you've disabled, enabling you to maintain a precise documentation of the security setup on your system.
How to Enable AppArmor Profile on Ubuntu 22.04
Re-Enabling a Disabled AppArmor Profile
The aa-enable command is useful in situations where an AppArmor profile that was previously disabled needs to be reactivated. Simple to use, this command makes sure the chosen profile's security policies are applied again by bringing it back to its active state.
The following is how to use this command:
sudo aa-enable /etc/apparmor.d/<profile-name>
The real name of the profile you want to enable should be substituted for <profile-name>.
Example: Enabling the usr.sbin.cupsd Profile
For instance, if you previously disabled the usr.sbin.cupsd profile, the command to re-enable it would be:
sudo aa-enable /etc/apparmor.d/usr.sbin.cupsdExample output:
Setting /etc/apparmor.d/usr.sbin.cupsd to enforce mode.This command will set the usr.sbin.cupsd profile to enforce mode. Enforce mode is crucial as it dictates that the security policies defined within the profile are actively applied, thus ensuring the intended security measures are in place.
Additional Commands with AppArmor Commands on Ubuntu 22.04
Using the aa-genprof Command
The command aa-genprof plays a crucial role in creating new AppArmor profiles. It is particularly helpful for applications that are not yet covered by existing profiles because it keeps track of an application's system calls and creates a profile based on this activity.
Example: Creating a Profile for Firefox
To start a fresh Firefox AppArmor profile, run:
sudo aa-genprof firefox
By capturing Firefox's system interactions, this command makes it easier to create a customized security profile.
Applying the aa-enforce Command
AppArmor profiles can be actively enforced with the aa-enforce command. It's especially useful after changing profiles because it instantly implements new policies without requiring a system restart.
Example: Enforcing All AppArmor Profiles
To impose all accessible profiles:
sudo aa-enforce /etc/apparmor.d/*
As an alternative, enforce a particular profile:
sudo aa-enforce /etc/apparmor.d/<profile-name>
Utilizing the aa-disable Command
A particular AppArmor profile can be deactivated using the aa-disable command. Disabling a profile allows its restrictions to be temporarily lifted, which is helpful when troubleshooting or giving an application more permissions.
Example: Disabling the Firefox Profile
In order to make the Firefox profile inactive,
sudo aa-disable /etc/apparmor.d/firefox
Remember that this is a temporary fix that will disappear if you restart the AppArmor service or reboot the system.
Implementing the aa-complain Command
A profile can be put in complain mode by using the aa-complain command. To facilitate testing and debugging, AppArmor logs restricted actions in this mode rather than blocking them.
Example: Switching to Complain Mode
To enter complain mode on the usr.sbin.cupsd profile:
sudo aa-complain /etc/apparmor.d/usr.sbin.cupsd
To observe its possible restrictions without enforcing them, replace usr.sbin.cupsd with the desired profile name.
Executing the aa-remove-unknown Command
When it comes to AppArmor profiles pertaining to unidentified or unused applications, the aa-remove-unknown command works wonders.
Example: Removing Unknown Profiles
To remove unknown profiles:
sudo aa-remove-unknown
By streamlining your AppArmor profiles, you can make sure your system always has an up-to-date security posture.
FAQs to Enable or Disable AppArmor on Ubuntu 22.04
Does disabling AppArmor pose any security risks on Ubuntu 22.04?
Disabling AppArmor may potentially expose the system to security vulnerabilities.
Can I configure specific permissions for applications with AppArmor on Ubuntu 22.04?
Yes, you can customize AppArmor profiles to control individual application permissions.
Where can I find logs related to AppArmor activities on Ubuntu 22.04?
AppArmor logs can be accessed in the system log files or security logs.
Is AppArmor pre-installed on Ubuntu 22.04 by default?
Yes, Ubuntu 22.04 comes with AppArmor as part of its default security features.
How can I restart AppArmor after making changes on Ubuntu 22.04?
You might need to restart the system to apply changes to AppArmor configurations.
Can I customize AppArmor profiles on Ubuntu 22.04?
Yes, profiles can be customized to allow or restrict specific application behaviors.
Is AppArmor compatible with all applications on Ubuntu 22.04?
Most applications work smoothly with AppArmor, but some may require adjustments for seamless operation.
Conclusion
We hope this tutorial helped you understand how to Enable or Disable AppArmor on Ubuntu 22.04.
If you have any queries, please leave a comment below, and we’ll be happy to respond to them for sure.

