Introduction
Before we begin talking about how to install Tripwire IDS on Debian 12, let's briefly understand – What is Tripwire IDS?
Tripwire IDS (Intrusion Detection System) is a powerful cybersecurity tool used to detect and prevent unauthorized access to computer networks. It monitors network activity, analyzing incoming and outgoing data for any suspicious or malicious behavior.
By comparing the current state of files and system configurations to a baseline, Tripwire IDS can identify any changes or deviations that could signal a security breach. This proactive approach helps organizations thwart cyber attacks and protect their sensitive data from unauthorized access.
In this tutorial, you will install Tripwire IDS on Debian 12. We will also address a few FAQs on how to install Tripwire IDS on Debian 12.
Advantages of Tripwire IDS
- Intrusion Detection: Tripwire IDS detects and alerts you about potential intrusions or unauthorized access to your network, keeping your system secure.
- File Integrity Monitoring: It monitors and alerts you about any unauthorized changes to system files, protecting against tampering and ensuring data integrity.
- Compliance Auditing: Tripwire IDS helps you meet regulatory compliance requirements by tracking and reporting on system configuration changes.
- Real-time Monitoring: It provides real-time monitoring of network activity, allowing you to respond quickly to potential security threats.
- Proactive Defense: Tripwire IDS identifies vulnerabilities before they can be exploited, helping you stay ahead of cyber threats and prevent breaches.
Tripwire Pre-Installation Steps on Debian 12
Before adding any new software, make sure your Debian system is up to date. This procedure guarantees a smooth software installation process in addition to improving system security. Let's go over how to get your Debian system ready for the Tripwire installation.
Updating the Package Database
To begin with, launch your terminal and start the package list updating procedure. Execute the subsequent command:
sudo apt update
By using this command, you can make sure that your system's package list is up-to-date with the most recent versions of the packages that are available. Making sure you install the safest and most recent version of the software is essential.
Upgrading Installed Packages
The next step is to upgrade any out-of-date packages on your system now that your package lists are current.
Run the subsequent command to initiate this procedure:
sudo apt upgrade
This command looks for any packages on your system that need updates and asks you to confirm before allowing the update to be applied.
Install Tripwire on Debian 12 via APT
Step 1: Run Tripwire IDS Installation Command on Debian
Being included in the default repositories of Debian makes installation easier. Start by running the following command:
sudo apt install tripwire
Step 2: Addressing the Initial Tripwire Configuration Prompts
When the installation starts, a Tripwire configuration dialog box will show up. This dialog highlights how important it is to use Tripwire's paired keys to verify the integrity of different files and make sure they are not altered. It's critical to realize that these keys may become briefly visible to hackers if your system has been seriously compromised. Verifying your network's security is crucial as a result.
Press (TAB) to move through the dialog until the (Ok) option is highlighted. To continue, hit Enter.
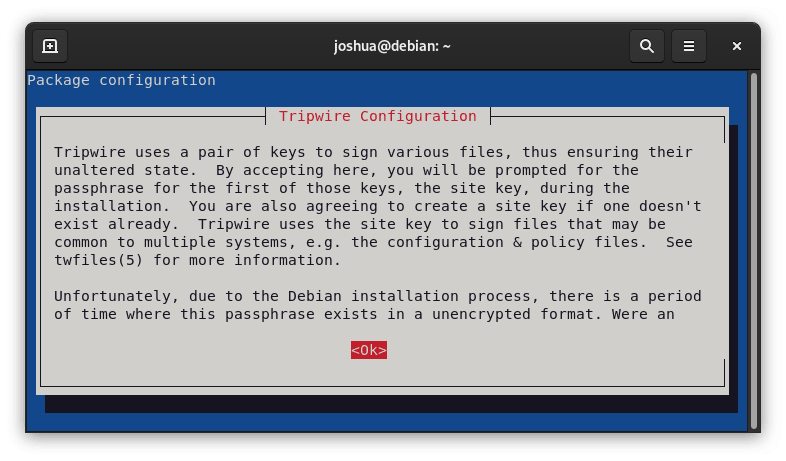
You will then be prompted by the system to create a site key passphrase. It is advised that you complete this during the current setup stage.
To create a site key passphrase and continue with the installation, select <Yes>.
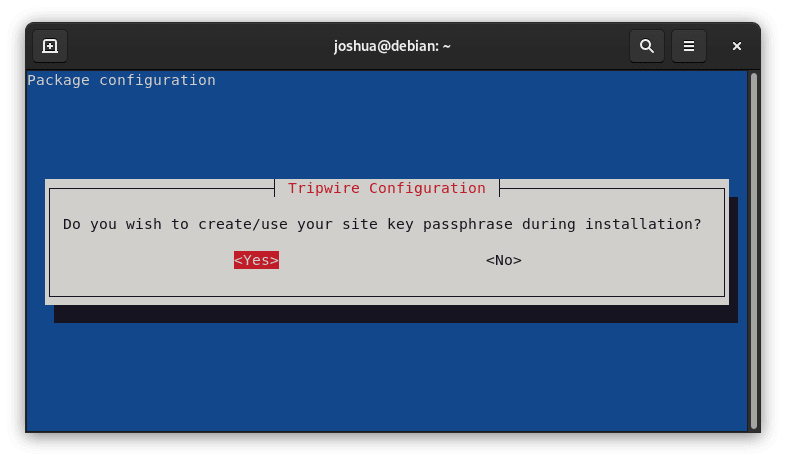
An additional warning appears, reinforcing the keys' temporary susceptibility during setup. Network security must be maintained, particularly in large network environments where local users may be able to intercept data.
Continue, hit enter after emphasizing the (Ok) option with (TAB).

You'll be prompted to create a local key passphrase in the dialog that appears. It's important to remember that this passphrase is different from the site key passphrase and that you shouldn't use them interchangeably.
To create a local key passphrase and continue, select <Yes> .
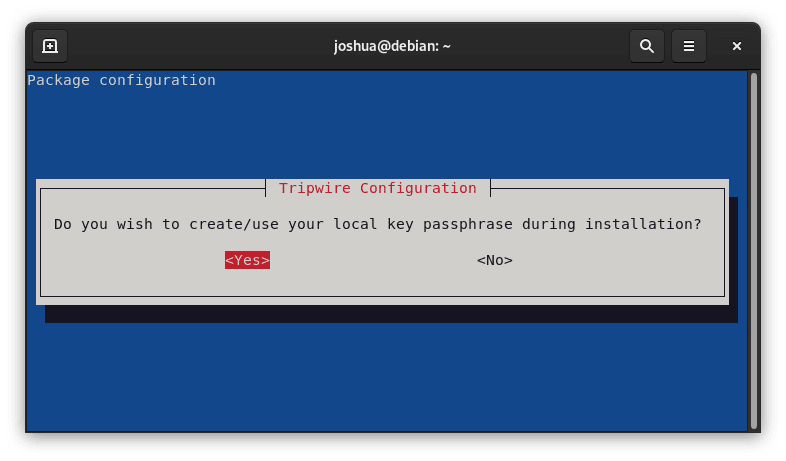
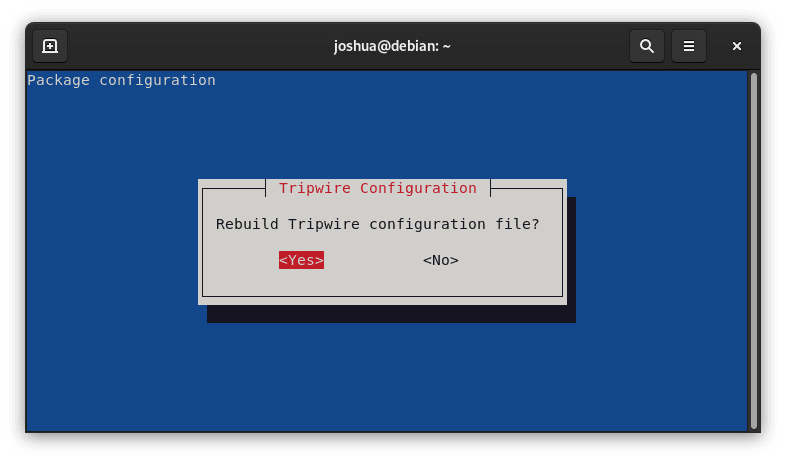
Step 3: Modifying the Tripwire Configuration
You have to reconstruct the you'llwire configuration file during this phase.
Click <Yes> to proceed.
The system will then offer details on Tripwire's monitoring attributes, file change procedures, and operational approach.
Press (TAB) to choose the (Ok) option, and then enter to proceed.

You'll then need to update the Tripwire policy file.
To proceed with the installation, select <Yes>.

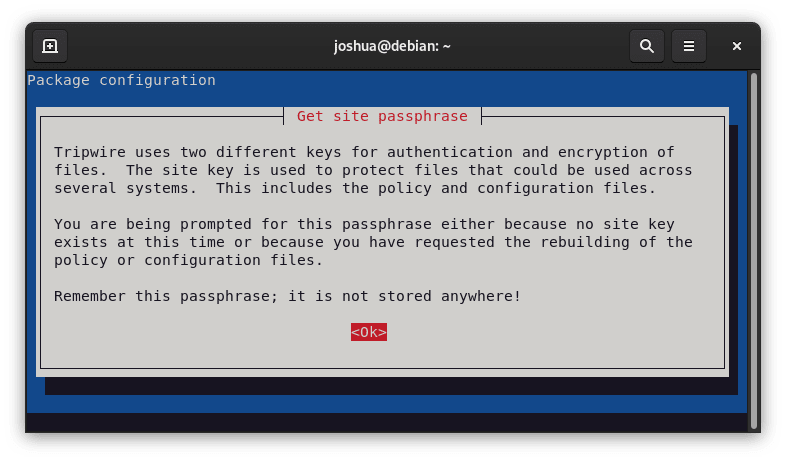
Step 4: Key Authentication in Tripwire
You will be informed via an informative dialog that Tripwire uses two different keys for authentication. It is essential to record this passphrase.
Press (TAB) until the (Ok) option is highlighted, then press enter to continue.
You will be prompted by the system to enter the site passphrase.
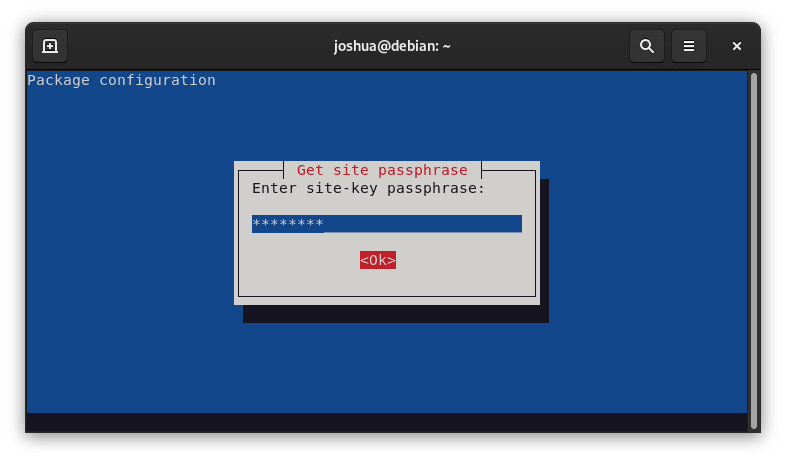
Finally, to confirm it:

The same message will show up again later, but this time it will be about the local passphrase.
Press (TAB) and choose the (Ok) option to navigate.
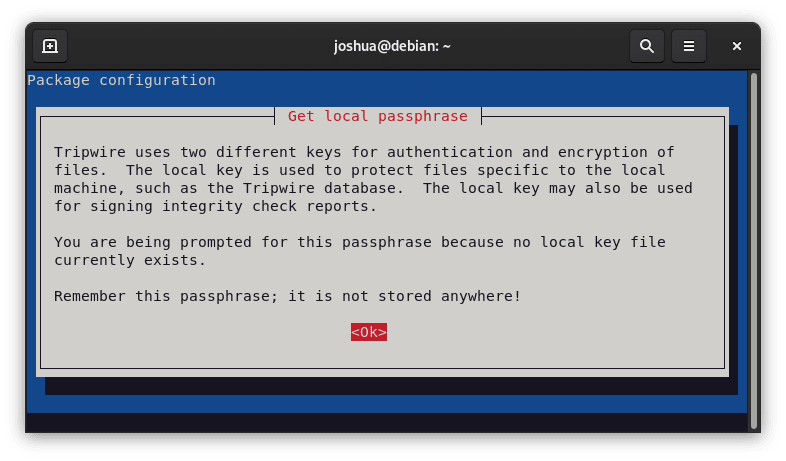
Enter the local passphrase in here:
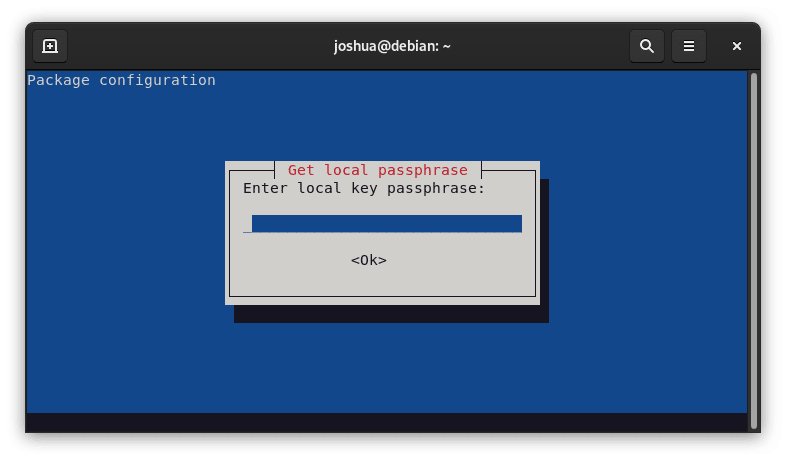
And confirm it once more:
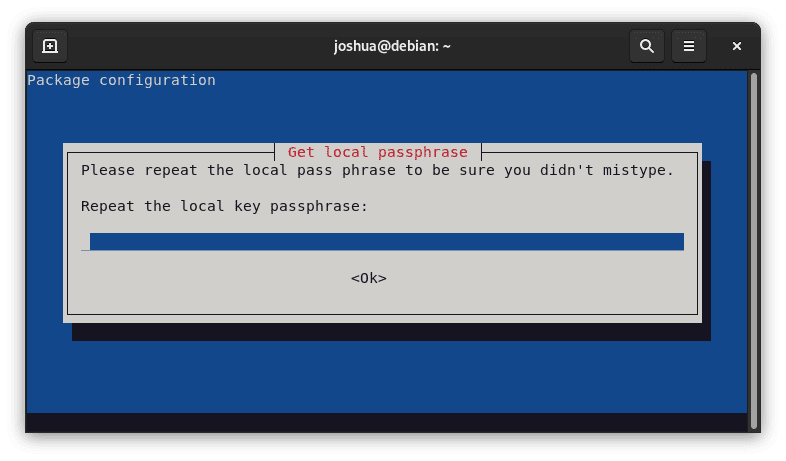
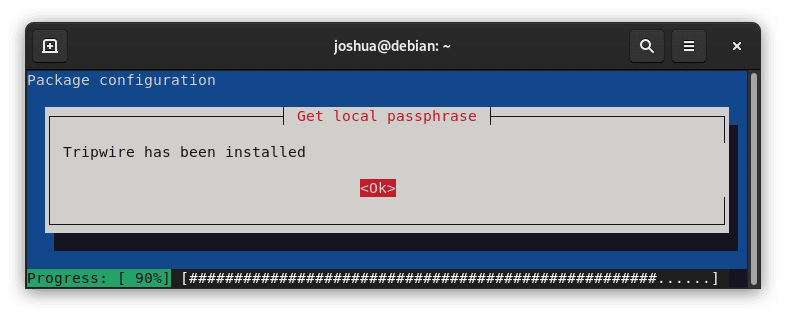
A confirmation message confirming Tripwire's successful installation will appear after completing these steps.
Configure Tripwire on Debian 12
Step 1: Configuring Tripwire Keys and Starting the Database
Setting up Tripwire is a crucial step to strengthen your Debian system's security defenses. Start by creating the Tripwire keys and setting up the database. While Debian offers a number of text editors, we'll be using nano for the purposes of this guide.
To begin, go to the we'llwire directory:
cd /etc/tripwire/
Then, launch the configuration file twcfg.txt:
sudo nano twcfg.txt
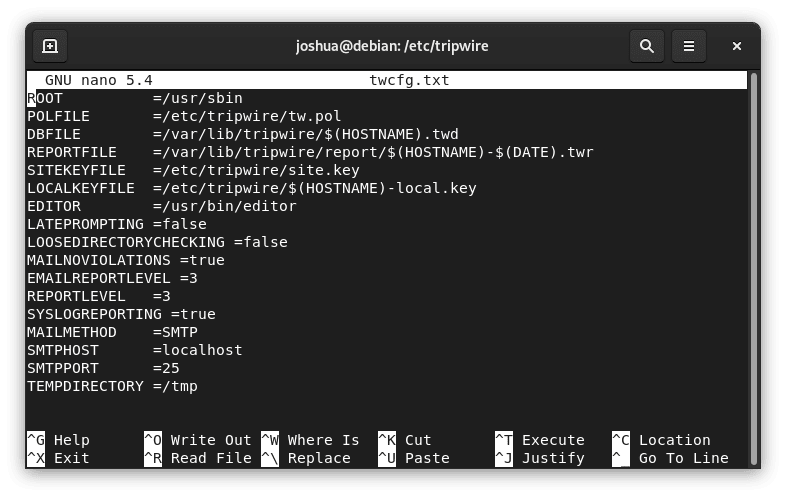
Usually, these default settings are adequate, but we advise changing REPORTLEVEL from 3 to 4. After making this adjustment, press (CTRL+O) to save the changes and (CTRL+X) to exit.
Run the following to create a new configuration file:
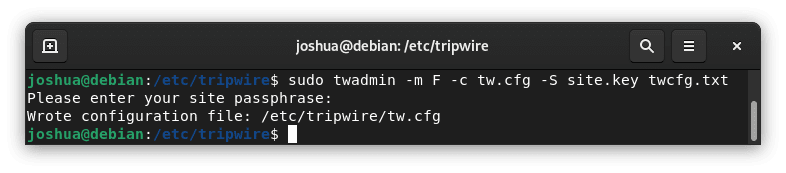
sudo twadmin -m F -c tw.cfg -S site.key twcfg.txt
You will then be prompted by the system to enter your site passphrase:
Step 2: Optimizing Tripwire Policy with Nano
To adjust the Tripwire policy, create the file twpolmake.pl in the nano editor:
sudo nano twpolmake.pl
Next, add the subsequent code to your file:
#!/usr/bin/perl
$POLFILE=$ARGV[0];
open(POL,"$POLFILE") or die "open error: $POLFILE" ;
my($myhost,$thost) ;
my($sharp,$tpath,$cond) ;
my($INRULE) = 0 ;
while () {
chomp; if (($thost) = /^HOSTNAME\s*=\s*(.*)\s*;/) {
$myhost = `hostname` ; chomp($myhost) ;
if ($thost ne $myhost) {
$_="HOSTNAME=\"$myhost\";" ;
}
}
elsif ( /^{/ ) {
$INRULE=1 ;
} elsif ( /^}/ ) {
$INRULE=0 ;
}
elsif ($INRULE == 1 and ($sharp,$tpath,$cond) = /^(\s*\#?\s*)(\/\S+)\b(\s+->\s+.+)$/) {
$ret = ($sharp =~ s/\#//g) ;
if ($tpath eq '/sbin/e2fsadm' ) {
$cond =~ s/;\s+(tune2fs.*)$/; \#$1/ ;
}
if (! -s $tpath) {
$_ = "$sharp#$tpath$cond" if ($ret == 0) ;
}
else {
$_ = "$sharp$tpath$cond" ;
}
}
print "$_\n" ;
}
close(POL) ;
In this file, paste the given Perl script. After you're sure you entered the script correctly, use CTRL+O to save the changes and CTRL+X to exit the editor.
To continue, go to the root account if you're using the SUDO command:
su
Create the configuration file after that:
perl twpolmake.pl twpol.txt > twpol.txt.new /
sudo twadmin -m P -c tw.cfg -p tw.pol -S site.key twpol.txt.new
Add sudo before the command if you get an error saying twadmin is not recognized.
Step 3: Tripwire Database Creation and Maintenance
After setting up the configurations, make a new Tripwire database:
sudo tripwire -m i -s -c tw.cfg
Use the following to see the recently created database:
sudo twprint -m d -d /var/lib/tripwire/debian.twd
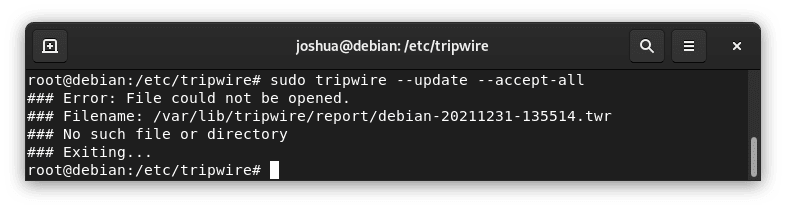
Preserving the accuracy of the database is essential. To update the Pwire IDS database of a database, run:
sudo tripwire --update --accept-all
Step 4: Testing and Reviewing Tripwire System
It is advisable to confirm the functionality of the Tripwire system. You can start a system by doing the following:
sudo tripwire -m c -s -c /etc/tripwire/tw.cfg
Tripwire stores its reports by default in the directory located at /var/lib/tripwire/report/. Open this link and make a list of the reports:
cd /var/lib/tripwire/report/ && ls
Use the print command to view a specific report by substituting the name of the desired report for <report file name>.
sudo twprint -m r -t 4 -r /var/lib/tripwire/report/<report file name>.twr
Verifying Tripwire IDS Freport’slity on Debian 12
Step 1: Testing with Sample Files
Verify Tripwire's functionality after installing and configuring it successfully on your Debian system. Making sample files and asking Tripwire to find them is one useful method for making sure the system is working.
To begin, create a few test files:
sudo touch test1 test2 test3
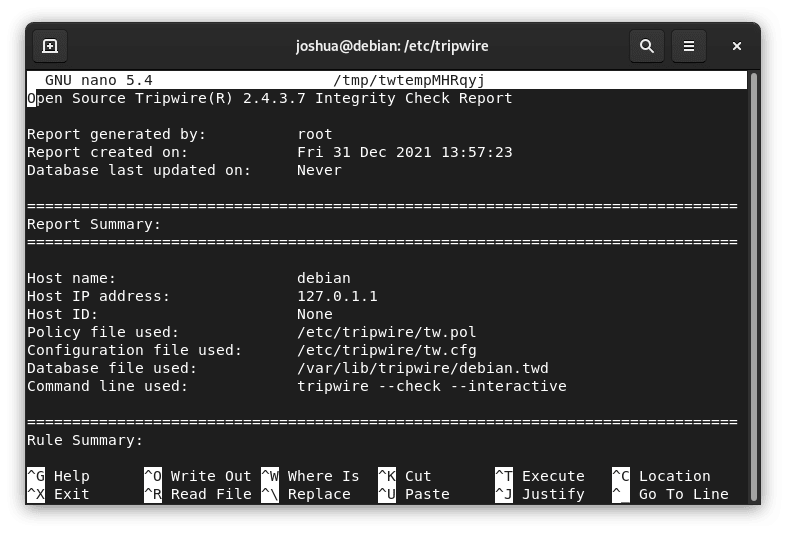
After setting up the sample files, launch Tripwire to test its detection capabilities:
sudo tripwire --check --interactive
The newly created files should be visible in the system's feedback if Tripwire runs smoothly.
Step 2: Access system reports on the wire
You are always welcome to review the generated reports for future reference or to confirm any activity. Use the following command to accomplish this, making sure to substitute the exact name of the report you're interested in for <report file name>:
sudo twprint --print-report --twrfile /var/lib/tripwire/report/<report file name>.twr
Setting up Tripwiyou’re Cronjob on Debian 12
Step 1: Scheduling Regular Tripwire Reports
For optimal Tripwire operation, set up a cronjob to generate reports automatically at predetermined intervals. Regular monitoring ensures that system changes are quickly identified, expediting the procedure.
To begin with, launch the crontab editor by using the following command:
sudo crontab -e
Choose the frequency at which you would like Tripwire to run its reports after that. You may be unsure of how to set up your timing, Crontab.Guru is a fantastic source of help for you.
To set Tripwire to check every 12 hours, for example, you would add the following line:
00 */12 * * * /usr/sbin/tripwire --check
Tripwire will generate and store the reports in the designated directory after it has finished its checks.
/var/lib/tripwire/report/
FAQs to Install Tripwire IDS on Debian 12
What are the system requirements for Tripwire IDS on Debian 12?
Tripwire IDS has modest system requirements. Debian 12 should meet the necessary criteria, such as sufficient disk space, memory, and processing power.
How does Tripwire IDS protect my system?
Tripwire IDS protects your system by monitoring network activity, detecting and alerting you about any unauthorized access or changes to system files, ensuring data integrity and security.
Can I customize Tripwire IDS to fit my specific needs?
Yes, you can customize Tripwire IDS to fit your specific requirements. You can configure it to monitor specific files, directories, or network activity based on your security needs.
Does Tripwire IDS provide real-time monitoring?
Yes, Tripwire IDS offers real-time monitoring of network activity, providing immediate alerts and notifications about potential security threats.
How often should I update Tripwire IDS on Debian 12?
It is recommended to keep Tripwire IDS up to date by checking for updates regularly. This ensures you have the latest security patches and improvements.
Can Tripwire IDS be integrated with other security tools?
Yes, Tripwire IDS can be integrated with other security tools and systems like Security Information and Event Management (SIEM) solutions, enhancing your overall cybersecurity infrastructure.
Does Tripwire IDS support automated reporting?
Yes, Tripwire IDS supports automated reporting, allowing you to generate reports on system integrity, compliance, and detected threats either on-demand or on a scheduled basis.
Conclusion
We hope this tutorial helped you understand how to install Tripwire IDS on Debian 12.
If you have any queries, please leave a comment below, and we’ll be happy to respond to them for sure.