Introduction
The rise of Infrastructure as Code (IaC) has revolutionized how organizations manage their IT infrastructure, but it also introduces significant security risks. Common issues such as vulnerabilities in IaC templates and misconfigurations can lead to serious breaches and data exposure.
Implementing effective security practices is crucial to mitigating these risks and safeguarding your infrastructure. This article explores best practices and real-world examples to enhance the security of your IaC deployments.
Importance of Securing IaC
Securing Infrastructure as Code (IaC) is crucial in today’s cloud-driven environments, where IaC adoption is rapidly growing. IaC allows for efficient and consistent provisioning of infrastructure, but it also introduces significant security risks. Vulnerabilities in IaC templates can lead to misconfigurations, making systems vulnerable to attacks.
Statistics show that IaC vulnerabilities are increasingly exploited, leading to breaches and downtime. Without proper security measures, these risks can have severe consequences for organizations, including data loss, compliance failures, and financial penalties.
Additionally, the dynamic nature of IaC makes it susceptible to configuration drifts—manual changes that deviate from the original configuration. This can lead to inconsistencies and security gaps, especially in large, complex environments. Effective secrets management, secure communication channels, and strict user access control are essential to mitigating these risks.
Moreover, poor visibility into IaC environments can result in "ghost resources", unused, unmonitored infrastructure that remains vulnerable to exploitation. Proper tagging and regular audits are necessary to maintain control over these resources.
Common Security Risks in IaC
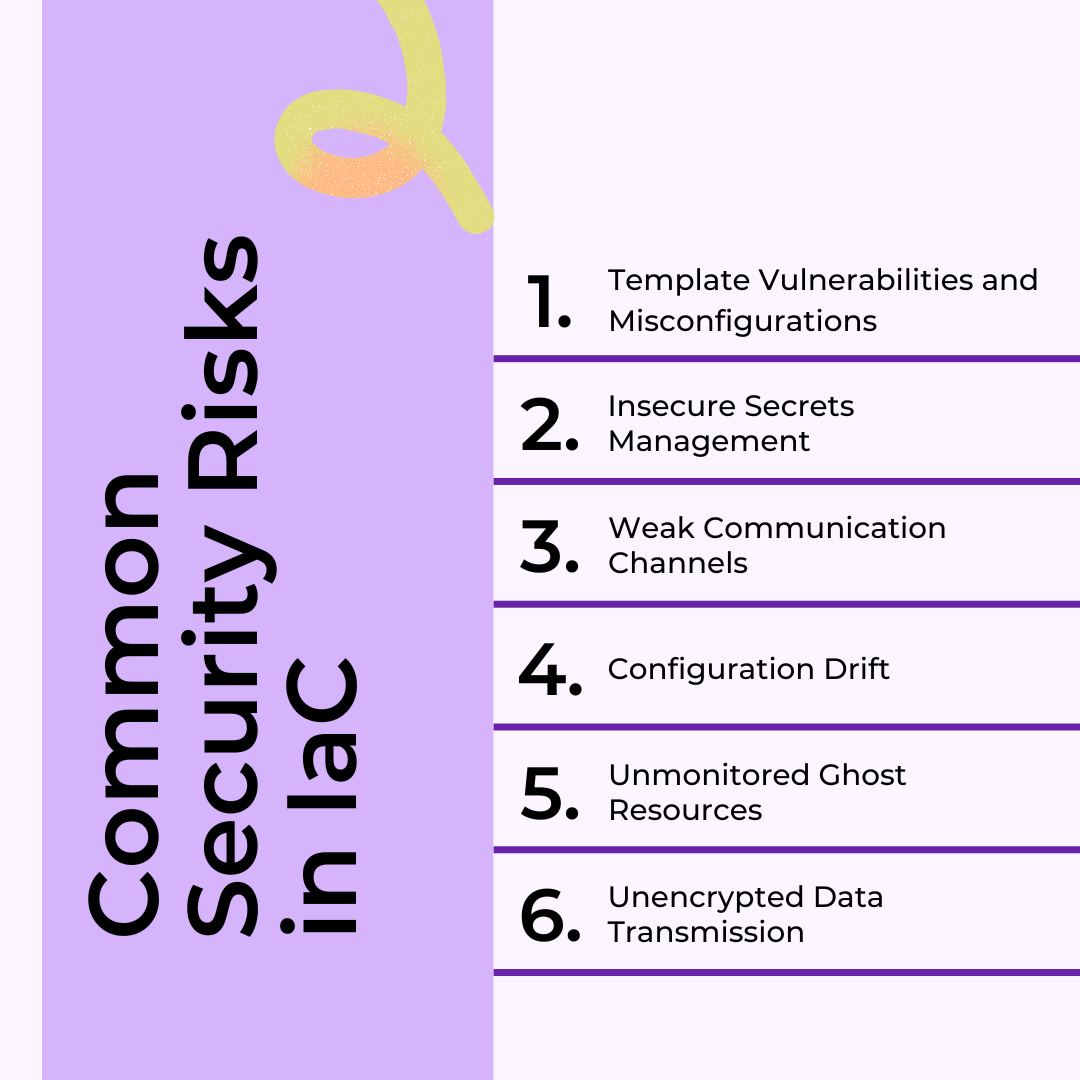
When implementing Infrastructure as Code (IaC), understanding the common security risks is crucial to safeguarding your environment. One major risk lies in IaC templates, where vulnerabilities or misconfigurations can lead to security breaches. Managing secrets securely is another challenge; hardcoding credentials or leaving them unprotected exposes critical data.
Communication channels between IaC components, especially master-node connections, need encryption and authentication to prevent unauthorized access. Similarly, user access management should follow the least privilege principle to reduce exposure. Another risk is configuration drifts, which occur when manual changes deviate from the intended configuration, creating inconsistencies that can lead to vulnerabilities.
Unmonitored ghost resources—infrastructure that remains active but unused—pose another threat, often being forgotten and left unsecured. Proper resource tagging and regular audits can mitigate this risk.
Additionally, data transmission risks can be minimized through encryption and secure protocols, ensuring sensitive information isn’t exposed during transit. Finally, maintaining comprehensive audit logs is essential for tracking changes, monitoring activities, and responding to incidents swiftly.
Best Practices for Securing IaC
Securing Infrastructure as Code (IaC) requires a blend of robust tools and best practices to protect your infrastructure from vulnerabilities. Start by integrating security plug-ins into your Integrated Development Environment (IDE) to catch issues early.
Implement continuous monitoring in production environments to ensure ongoing compliance and security. Use sandbox environments for safe testing before deployment, and conduct static code analysis to identify security flaws in IaC templates.
Regular patch management is essential to address newly discovered vulnerabilities promptly. Adhering to compliance standards, such as those mandated by industry regulations, ensures that your IaC environment meets all necessary security requirements. By following these best practices, organizations can effectively reduce risks and maintain a secure IaC framework.
Tools for Securing IaC
To secure Infrastructure as Code (IaC) effectively, leveraging the right tools is essential. IaC provisioning tools like Terraform and AWS CloudFormation help automate infrastructure deployment while incorporating security best practices.
Configuration management tools such as Ansible, Chef, and Puppet ensure consistent configurations across environments, reducing the risk of misconfigurations.
Security tools are vital for ensuring the protection of your IaC deployments. Cloud Access Security Brokers (CASBs) monitor and control access to cloud services, while SSL and VPNs ensure secure communication. Combining these tools creates a fortified environment, protecting your infrastructure from vulnerabilities.
Case Studies/Examples
Real-world Examples:
- Capital One Data Breach (2019): Capital One suffered a massive data breach due to a vulnerability in their IaC templates. The breach compromised the sensitive data of more than 100 million customers. The vulnerability was caused by an improperly configured firewall rule within their AWS CloudFormation templates, which allowed an attacker to access sensitive data stored in S3 buckets.
- Tesla's Ransomware Attack (2020): Tesla experienced a ransomware attack where attackers exploited weaknesses in their IaC configurations. The attackers gained access through insecure endpoints exposed in their Terraform templates. This incident highlighted the risks associated with insufficient security controls and the importance of securing IaC environments to prevent unauthorized access.
Successful Implementations:
- Netflix’s IaC Security: Netflix is known for its robust IaC security practices. They use a combination of automated security scans, continuous monitoring, and a well-defined process for managing IaC configurations. By integrating security checks into their CI/CD pipelines and using tools like Security Monkey, Netflix has managed to effectively reduce vulnerabilities and ensure a secure infrastructure.
- Shopify's Compliance and Security: Shopify has implemented rigorous IaC security measures, including static code analysis and automated policy enforcement. They use tools like Terraform for IaC provisioning and incorporate security plug-ins into their development workflows. This proactive approach has helped Shopify maintain a secure and compliant infrastructure, avoiding many common pitfalls associated with IaC deployments.
Key Takeaways
- IaC Adoption Risks: Increased use of IaC introduces significant security risks due to common vulnerabilities and misconfigurations.
- Best Practices Essential: Implementing best practices such as static code analysis, continuous monitoring, and using sandbox environments is crucial for securing IaC.
- Common Threats: Key risks include exposed secrets, misconfigured templates, and communication vulnerabilities.
- Successful Strategies: Effective security measures include integrating security plug-ins, applying the least privilege principle, and maintaining thorough audit logs.
- Real-World Lessons: Both failures and successes in IaC security highlight the importance of following established security protocols and using appropriate tools.
Conclusion
Securing Infrastructure as Code (IaC) is vital as IaC adoption grows, bringing increased security risks. Key practices include addressing vulnerabilities, integrating security tools, and maintaining continuous monitoring. Learning from real-world cases of both failures and successes underscores the importance of proactive measures and adherence to best practices.
To enhance IaC security, regularly review and update security practices, stay informed about new threats, and consider expert consultation. These steps will help protect sensitive information and ensure a secure infrastructure.


