Introduction
In today’s fast-paced development environment, securing your CI/CD pipeline is more crucial than ever. Traditional security measures often lag behind the rapid pace of deployment, leaving vulnerabilities exposed.
Without integrated security practices, your pipeline is at constant risk. The solution? Implementing DevSecOps. By embedding security throughout your CI/CD process, you ensure continuous protection, adapt to evolving threats, and maintain a robust defense against potential breaches.
The CI/CD Pipeline Overview
A CI/CD pipeline is a crucial component in modern software development, designed to automate and streamline the process of integrating and delivering code.
CI, or Continuous Integration, involves automatically building and testing code changes as they are committed to the repository. This process ensures that new code integrates seamlessly with existing code, catching issues early and improving code quality.
Continuous Deployment (CD) and Continuous Delivery are the final stages that highlight the automation of the release process. Continuous Deployment automatically pushes changes to production once they pass automated tests, facilitating rapid and reliable updates.
Continuous Delivery, on the other hand, ensures that code changes are ready for deployment but may require manual approval before going live. Both approaches enhance efficiency and reduce the time between writing code and delivering it to users.
The benefits of a CI/CD pipeline are substantial. It accelerates the development lifecycle by automating repetitive tasks, reduces human error, and ensures consistent and reliable releases.
By integrating automated testing and deployment, development teams can quickly respond to changes, fix bugs, and deliver new features faster, all while maintaining high quality and stability in their applications.
However, with these advantages come challenges, especially when it comes to security. As development speed increases, so does the potential for vulnerabilities if security is not integrated into every stage of the pipeline. This is where DevSecOps comes into play, ensuring that security is embedded throughout the CI/CD process, safeguarding your pipeline against potential threats.
Integrating Security into CI/CD Pipelines
Integrating security into CI/CD pipelines is essential for safeguarding your development process from vulnerabilities and threats.
The concept of Shift-Left Security is fundamental here; it involves incorporating security measures early in the development lifecycle rather than addressing them at the end. By identifying and addressing security issues during the coding phase, you can mitigate risks before they propagate through the pipeline.
Automation of Security Checks is another critical aspect. Automated tools and scripts can continuously scan for vulnerabilities in code, dependencies, and configurations. For example, tools like static application security testing (SAST) can analyze code for potential security flaws, while dynamic application security testing (DAST) can examine running applications for vulnerabilities. Integrating these tools into your CI/CD pipeline ensures that security checks are performed consistently and promptly.
Continuous Monitoring is essential for maintaining security throughout the pipeline. This involves real-time monitoring of code, infrastructure, and deployments to detect and respond to potential security incidents. Implementing continuous security monitoring tools helps track suspicious activities and vulnerabilities, allowing for immediate action to address issues before they impact production.
Key Strategies for Securing Your CI/CD Pipeline
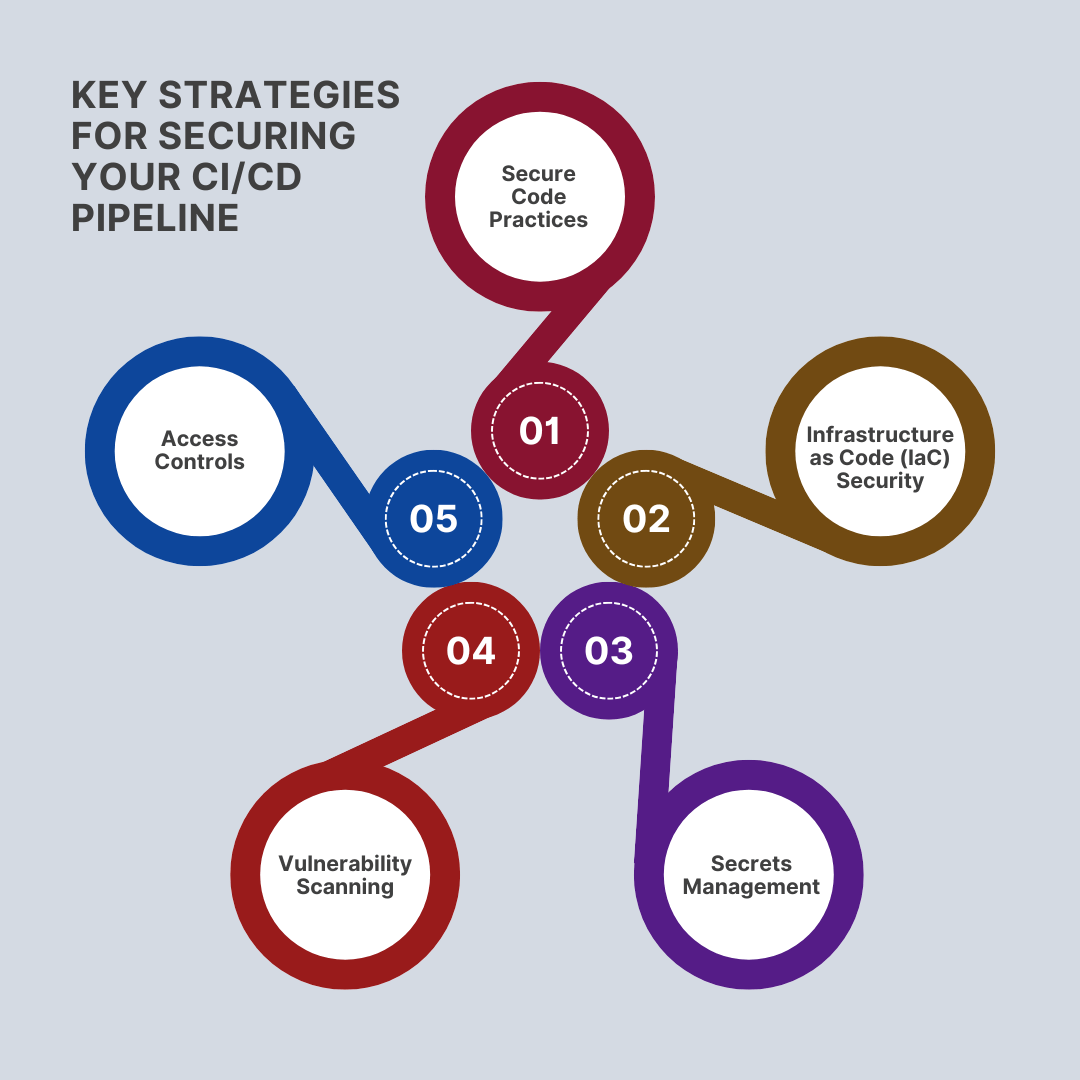
Securing your CI/CD pipeline requires a multi-faceted approach to address various aspects of the development and deployment process. Following are some crucial strategies to apply:
Secure Code Practices: Start by incorporating security into your coding practices. Conducting regular code reviews and using static analysis tools help identify vulnerabilities early on. Use tools to identify insecure coding practices and ensure compliance with secure coding standards. Additionally, manage dependencies carefully by monitoring and updating third-party libraries to address known vulnerabilities.
Infrastructure as Code (IaC) Security: IaC allows you to manage infrastructure through code, making it essential to include security practices in this area. Implement best practices for secure configuration and use automated tools to scan IaC templates for vulnerabilities. Ensure that your IaC scripts follow security guidelines and are regularly reviewed and tested.
Secrets Management: Always handle sensitive information, including API keys, passwords, and tokens, with care. Use dedicated secrets management tools to securely store and access secrets, avoiding hard-coded values in your codebase. Implement access controls to limit who can view or modify secrets, ensuring that sensitive information remains protected.
Vulnerability Scanning: Integrate vulnerability scanning tools into your pipeline to continuously assess both code and deployed applications for security flaws. Regularly conducting scans helps identify and address vulnerabilities before they can be exploited. Automate these scans to ensure that vulnerabilities are identified and remediated promptly.
Access Controls: Enforce strict access controls to safeguard your pipeline and associated systems. Implement role-based access controls (RBAC) to limit permissions according to user roles. Use multi-factor authentication (MFA) to enhance security for accessing critical systems and data.
Tools and Technologies
Effective integration of security into CI/CD pipelines relies on the right tools and technologies. Here’s a look at essential tools and how they can be integrated into your CI/CD processes:
Security Tools: A variety of tools are available to enhance security within your CI/CD pipeline. Static Application Security Testing (SAST) tools, like SonarQube and Checkmarx, analyze source code for vulnerabilities without executing the program.
Dynamic Application Security Testing (DAST) tools, such as OWASP ZAP and Burp Suite, test running applications for potential security issues. Container security tools like Aqua Security and Sysdig focus on securing containerized environments and images.
CI/CD Integrations: Many CI/CD platforms support integration with security tools to automate vulnerability assessments. For instance, Jenkins can integrate with SAST tools through plugins, enabling automated code scanning during the build process.
GitLab CI offers built-in security scanning features, including SAST and dependency scanning, that can be easily configured within the CI/CD pipeline. CircleCI and GitHub Actions also support integrations with a range of security tools to enforce security checks.
Case Studies: Real-world examples highlight the benefits of these tools. For instance, Netflix uses Aqua Security to secure its extensive container infrastructure, ensuring robust security across its global deployments.
Google integrates OWASP ZAP into its CI/CD pipeline to automate security testing, enabling rapid detection and remediation of vulnerabilities in its applications.
Best Practices for Implementation
Implementing DevSecOps effectively requires a strategic approach and adherence to best practices. Following are the key practices to ensure successful integration:
Develop a Security Culture: Cultivating a security-first mindset across your development team is crucial. Promote collaboration among development, operations, and security teams to create a culture where security is everyone's responsibility. Regularly communicate the importance of security and integrate it into daily workflows to build a proactive security posture.
Training and Awareness: Invest in training programs to educate your team on DevSecOps practices and security best practices. Provide regular workshops and resources on topics like secure coding, vulnerability management, and threat modeling. Keeping your team updated on emerging security threats and new tools helps them stay vigilant and responsive to potential risks.
Iterative Improvement: DevSecOps is not a one-time implementation; rather, it is an ongoing process. Continuously assess and refine your security practices based on feedback and evolving threats. Implement a feedback loop where security incidents and vulnerabilities are analyzed to improve processes and tools. Regularly update security policies and practices to adapt to new challenges and ensure the pipeline remains robust and secure.
Common Challenges and Solutions
Integrating DevSecOps into your CI/CD pipeline can present several challenges. Tackling these challenges is vital for ensuring a successful implementation.
Resistance to Change: One of the main hurdles is overcoming organizational resistance. Teams accustomed to traditional practices may be reluctant to adopt new security measures.
Solution: Promote the benefits of DevSecOps through clear communication and demonstrate how security integration enhances overall efficiency and reduces risk. Involve stakeholders early in the process and offer training to facilitate a smooth transition.
Complexity: The integration of security into CI/CD pipelines can introduce complexity, especially when dealing with multiple tools and technologies.
Solution: Simplify the process by choosing tools that offer seamless integration with your existing CI/CD platform. Standardize security practices and automate where possible to reduce manual intervention and streamline workflows.
Resource Constraints: Limited resources, such as budget constraints and lack of expertise, can significantly hinder the successful implementation of DevSecOps.
Solution: Prioritize security initiatives based on risk and impact. Leverage open-source tools and platforms that provide cost-effective solutions. Additionally, consider cloud-based security solutions that scale with your needs and provide access to advanced features without significant upfront investment.
Measuring Success
Evaluating the effectiveness of your DevSecOps implementation is crucial for continuous improvement and ensuring that security measures are achieving their intended goals. Here’s how to measure success:
Metrics: Establishing key performance indicators (KPIs) is essential for assessing the impact of your DevSecOps practices. Key metrics to track include:
- Vulnerability Detection Rate: Measure the number of vulnerabilities identified and resolved during the CI/CD process.
- Incident Response Time: Monitor the time required to detect, respond to, and resolve security incidents.
- Deployment Frequency: Monitor how often deployments occur and correlate this with the frequency of security issues to ensure that security does not impede development speed.
- False Positives/Negatives: Assess the accuracy of security tools to minimize false positives and negatives, ensuring they provide actionable insights.
Continuous Improvement: Use the data collected from these metrics to drive ongoing enhancements. Consistently review and analyze performance data to identify trends, strengths, and areas that need improvement. Incorporate feedback from security incidents and team input to refine processes, update security practices, and adjust tool configurations as required.
Feedback Loops: Implement feedback mechanisms to gather insights from all stakeholders involved in the DevSecOps process. Use this feedback to address any challenges, improve practices, and ensure alignment with organizational goals. Regularly update your DevSecOps strategy based on these insights to adapt to evolving threats and technology advancements.
Conclusion
Securing your CI/CD pipeline with DevSecOps is crucial for mitigating risks in modern development. Integrate security early in the process, automate checks, and use advanced tools to detect vulnerabilities proactively.
Foster a security-focused culture through team training and regular feedback. Measuring success with key metrics ensures continuous improvement and adaptation to new threats. By embedding security from the start, you enhance the resilience and efficiency of your software delivery process.

