Introduction
In the fast-moving development world today, security is often sidelined when integrating DevOps workflows. Neglecting this aspect can create major vulnerabilities and data breaches, putting both operations and customer trust at risk.
To address these risks, it’s crucial to embed robust security measures into every stage of the DevOps pipeline. By taking a proactive approach, organizations can protect their systems and ensure a resilient, secure infrastructure.
Understanding DevOps and Security Integration
DevOps is a methodology that merges development and operations to optimize software delivery and foster collaboration. It prioritizes automation, continuous integration, and continuous delivery (CI/CD) to speed up development cycles and improve software quality. However, this fast-paced environment often introduces unique security challenges.
Integrating security into DevOps, commonly referred to as DevSecOps, is essential to address these challenges effectively. Security must be a core element, integrated throughout the DevOps process, rather than an afterthought. The fundamental principle of DevSecOps is the Shift Left approach, which integrates security measures at the early stages of the development lifecycle. This proactive approach enables the identification and resolution of vulnerabilities before they develop into larger problems.
In a traditional DevOps workflow, security is frequently addressed only at the end of the development cycle, leading to potential vulnerabilities being discovered late in the process. This reactive strategy can cause costly setbacks and greater risk. By integrating security from the outset, DevSecOps ensures continuous security monitoring and threat detection, allowing for immediate responses to potential risks.
Beyond early integration, automation is a key element in DevSecOps. Automated security tools and practices ensure consistent and thorough security checks throughout the development pipeline. This includes automated testing for vulnerabilities, configuration management, and compliance monitoring.
Core Principles of Security-Enhanced DevOps
Securing a DevOps workflow involves adopting several core principles that ensure security is woven into every aspect of the development process. These principles focus on early integration, continuous monitoring, and automation, each playing a vital role in fortifying the security posture of DevOps environments.
Shift Left Approach: A core principle of security-focused DevOps is the "Shift Left" strategy. This approach emphasizes integrating security measures early in the development lifecycle, rather than waiting until later stages.
By addressing security from the start, potential vulnerabilities are identified and mitigated before they become costly issues. This proactive stance not only improves the security of the final product but also reduces the time and cost associated with late-stage fixes.
Continuous Security Monitoring: Continuous security monitoring is crucial in a DevOps environment where changes are frequent and rapid. This principle involves implementing real-time monitoring and threat detection systems that continuously assess the security posture of applications and infrastructure.
Tools and practices such as Security Information and Event Management (SIEM) systems, intrusion detection systems (IDS), and automated vulnerability scanners are essential for maintaining a vigilant security stance and responding swiftly to potential threats.
Automation and Security: Automation is a fundamental aspect of DevOps, and its integration with security is just as crucial. Automating security processes, such as code analysis, configuration checks, and compliance validation, ensures that security practices are consistently applied across the entire development pipeline.
Automated tools, such as Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST), facilitate continuous security assessments, enabling rapid identification and remediation of vulnerabilities.
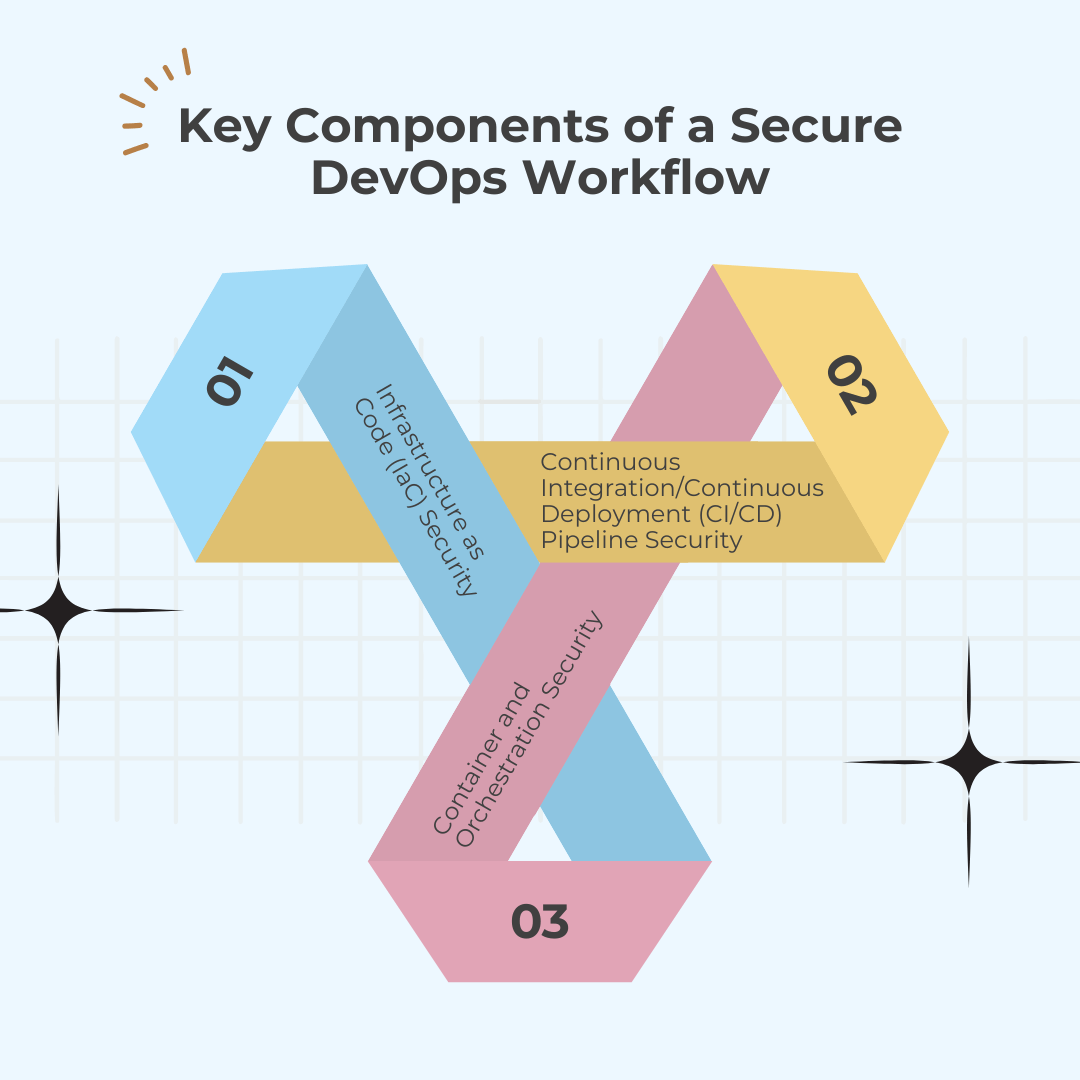
Key Components of a Secure DevOps Workflow
To achieve a secure DevOps workflow, several key components must be effectively integrated into the development and deployment processes. These components ensure that security is maintained across various aspects of the DevOps pipeline.
Infrastructure as Code (IaC) Security: Infrastructure as Code (IaC) enables the automated setup and management of infrastructure using code. While IaC enhances efficiency, it also introduces security risks if not properly managed.
Securing IaC involves using tools and practices to validate and monitor configurations, ensuring they adhere to security policies. Tools such as Terraform and AWS CloudFormation offer built-in security features and integrations with security scanning tools to identify and rectify vulnerabilities in infrastructure code before deployment.
Continuous Integration/Continuous Deployment (CI/CD) Pipeline Security: The CI/CD pipeline is the backbone of modern DevOps, automating the build, test, and deployment processes. Securing the CI/CD pipeline is crucial to prevent malicious code from being introduced and to protect the integrity of the pipeline.
This involves implementing security measures such as access controls, code reviews, and integrating security tools into the pipeline. Tools like Jenkins, GitLab CI/CD, and CircleCI offer plugins and integrations for security scanning and compliance checks to ensure that every stage of the pipeline adheres to security best practices.
Container and Orchestration Security: Containers and orchestration platforms like Docker and Kubernetes streamline application deployment and management but come with their own security concerns. Securing containers involves scanning container images for vulnerabilities, implementing runtime security measures, and adhering to best practices for container configuration.
Kubernetes security involves securing cluster configurations, managing access controls, and monitoring for security breaches. Tools like Docker Bench for Security and Kubernetes security best practices help mitigate risks associated with containerized applications and orchestration environments.
Best Practices for Implementing Security in DevOps
Implementing security effectively within a DevOps workflow requires adherence to best practices that integrate security seamlessly into every phase of the development process. These practices ensure that security measures are proactive, automated, and continuously monitored.
Automated Security Testing: One of the key practices for enhancing security in DevOps is the use of automated security testing. This encompasses both Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST).
SAST tools analyze source code or binaries for vulnerabilities early in the development cycle, while DAST tools assess applications during runtime to identify security issues that may not be visible in code. By incorporating these automated tests into the CI/CD pipeline, organizations can detect and address vulnerabilities promptly, reducing the risk of security flaws in production.
Configuration Management and Compliance: Proper configuration management is essential for maintaining a secure DevOps environment. This involves regularly reviewing and updating configuration files to adhere to security best practices and compliance standards.
Tools such as Ansible, Puppet, and Chef can automate configuration management and enforce security policies across infrastructure. Additionally, implementing infrastructure compliance tools ensures that configurations meet industry standards and regulatory requirements, minimizing the risk of misconfigurations and potential vulnerabilities.
Incident Response and Recovery: An effective incident response plan is critical for managing and mitigating the impact of security breaches. Developing a response plan involves defining roles and responsibilities, establishing communication protocols, and setting up mechanisms for rapid detection and response.
Regularly testing and updating the incident response plan ensures that the team is prepared to handle security incidents swiftly and effectively. Additionally, having a recovery plan in place, including data backups and disaster recovery procedures, helps minimize downtime and restore normal operations quickly after an incident.
Real-Life Case Studies
Case Study 1: Adobe's Secure DevOps Transformation
Adobe, a major player in digital media, faced challenges integrating security into its rapid DevOps practices. As the company adopted more frequent deployment cycles, ensuring security without compromising speed became a priority. Adobe implemented a DevSecOps strategy that integrated security practices early in the CI/CD pipeline.
They adopted automated security testing tools like SAST and DAST, which allowed them to identify vulnerabilities in code before it reached production. Additionally, Adobe used container security tools to monitor their Docker environments for potential threats.
The impact was significant. Adobe reported a dramatic reduction in security incidents and vulnerabilities discovered in production. By shifting security left and automating testing processes, Adobe improved both their security posture and development efficiency, demonstrating the benefits of integrating security seamlessly into DevOps workflows.
Case Study 2: Capital One’s Security Breach and Recovery
Capital One, a leading financial institution, experienced a major security breach in 2019 due to a misconfigured web application firewall in their AWS environment. The breach exposed sensitive customer data and highlighted gaps in their security practices within the DevOps workflow.
In response to the breach, Capital One undertook a comprehensive overhaul of their DevOps security practices. They implemented a robust security framework that included automated vulnerability scanning, enhanced configuration management, and continuous security monitoring. They also adopted improved incident response protocols and conducted regular security training for their DevOps teams.
The recovery process significantly strengthened their security posture. Capital One’s revamped security measures allowed them to better manage risks and comply with regulatory requirements. The case serves as a powerful example of how addressing security gaps and implementing best practices can enhance an organization’s overall security and resilience.
Challenges and Solutions
Integrating security into DevOps workflows presents several challenges, but addressing these issues proactively can lead to more robust and secure systems. Below are some typical obstacles and effective ways to address them:
Common Challenges
Resistance to Change: One of the primary challenges is resistance from teams accustomed to traditional development practices. Security is often perceived as an additional burden rather than a value-added component.
Integration Issues: Seamlessly integrating security tools into existing DevOps pipelines can be complex. Different tools may not always work well together, and configuring them can be time-consuming.
Skill Gaps: DevOps teams may lack the specialized skills needed for effective security implementation, leading to potential gaps in security practices and knowledge.
Practical Solutions
Foster a Security Culture: Overcoming resistance involves promoting a culture that values security as a core aspect of DevOps. This can be achieved by demonstrating the benefits of early security integration and involving security teams in planning and decision-making processes.
Providing training and resources to help teams understand the importance of security can also facilitate a smoother transition.
Adopt Integrated Security Tools: To address integration issues, choose security tools that offer compatibility with your existing DevOps tools and workflows. Many modern security tools are designed to integrate seamlessly with popular CI/CD platforms.
Additionally, leveraging platforms that provide comprehensive security solutions can help reduce the complexity of managing multiple tools.
Invest in Training and Development: Addressing skill gaps requires investing in ongoing training and development for your teams. Providing access to security training programs, certifications, and hands-on workshops can enhance the team's ability to implement and manage security practices effectively.
Encouraging cross-functional collaboration between development, operations, and security teams can also bridge knowledge gaps and improve overall security practices.
Tools and Resources
Incorporating security into DevOps workflows requires the right tools and resources to ensure effective and continuous protection. Here’s a guide to essential tools and additional resources that can enhance your DevSecOps practices:
Recommended Security Tools
Static Application Security Testing (SAST) Tools: SAST tools analyze source code for vulnerabilities before the code is executed.
Popular tools include SonarQube and Checkmarx, which help identify issues early in the development process, enabling developers to fix vulnerabilities before they reach production.
Dynamic Application Security Testing (DAST) Tools: DAST tools test applications during runtime to uncover vulnerabilities that may not be evident from source code alone.
Tools such as OWASP ZAP and Burp Suite offer comprehensive scanning capabilities to detect security issues in live applications.
Container Security Tools: To secure containerized environments, use tools like Aqua Security and Anchore.
These tools provide image scanning for vulnerabilities, runtime protection, and compliance checks to ensure the security of containers and orchestrated environments like Kubernetes.
Configuration Management and Compliance Tools: Tools like Terraform and Chef facilitate secure and compliant infrastructure management.
They help enforce security policies and configurations consistently across environments, reducing the risk of misconfigurations.
Continuous Security Monitoring Tools: For real-time monitoring and threat detection, Splunk and Elastic Security offer comprehensive solutions.
These tools provide visibility into security events, enabling rapid response to potential threats.
Key Takeaways
- Integrate Security Early: Adopt a "Shift Left" approach to incorporate security measures from the start of the DevOps pipeline, reducing vulnerabilities before deployment.
- Automate Security Practices: Use automated tools for SAST, DAST, and container security to ensure consistent and efficient security assessments throughout the development lifecycle.
- Continuous Monitoring: Implement real-time security monitoring and threat detection to quickly identify and respond to potential security issues.
- Adopt Best Practices: Follow best practices for configuration management, compliance, and incident response to enhance security and resilience in your DevOps workflow.
- Leverage Tools and Resources: Utilize recommended security tools and resources, including training and industry reports, to stay updated and effectively manage security within DevOps environments.
Conclusion
Integrating security into DevOps workflows is crucial for protecting applications and infrastructure. By adopting core principles like shifting security left, continuous monitoring, and automation, organizations can proactively address vulnerabilities and enhance their security posture.
Real-life examples from Adobe and Capital One highlight the benefits of these practices, demonstrating improved security and operational efficiency. While challenges such as resistance to change and integration issues exist, addressing them with targeted solutions ensures a successful security integration. Prioritizing security within DevOps not only protects systems but also boosts overall development efficiency, leading to a more resilient and secure environment.

