Introduction
In today’s development landscape, CI/CD pipelines are crucial for efficient software delivery but also present significant security risks. With increasing threats like unauthorized access and code injection, safeguarding these environments is essential.
To address these concerns, this article explores best practices for defending against security threats in CI/CD pipelines. Learn how to implement robust security measures to protect your development process and ensure a secure and reliable software deployment.
Understanding CI/CD and Security Threats
What is CI/CD?
Continuous Integration (CI) and Continuous Deployment (CD) are methods that enhance software development efficiency through automation and optimization. Continuous Integration (CI) focuses on the regular integration of code changes into a shared repository, utilizing automated builds and tests to catch issues early. CD builds on this by automating the deployment phase, ensuring that code changes are consistently and quickly delivered to production. Together, CI/CD enables faster development cycles and reliable software delivery.
Common Security Threats in CI/CD
Despite its benefits, the CI/CD process introduces several security vulnerabilities:
- Unauthorized Access: Gaining access to CI/CD tools or repositories without proper authorization can lead to unauthorized code changes, data leaks, or system breaches.
- Code Injection: Malicious actors might exploit vulnerabilities in the CI/CD pipeline to inject harmful code or scripts, potentially compromising the entire application.
- Data Breaches: Sensitive information, including API keys and credentials, often resides within the CI/CD environment. Insufficient protection of this data can lead to breaches and exploitation.
- Misconfigurations: Incorrectly configured CI/CD pipelines or related tools can expose systems to attacks, either through insecure default settings or improper access controls.
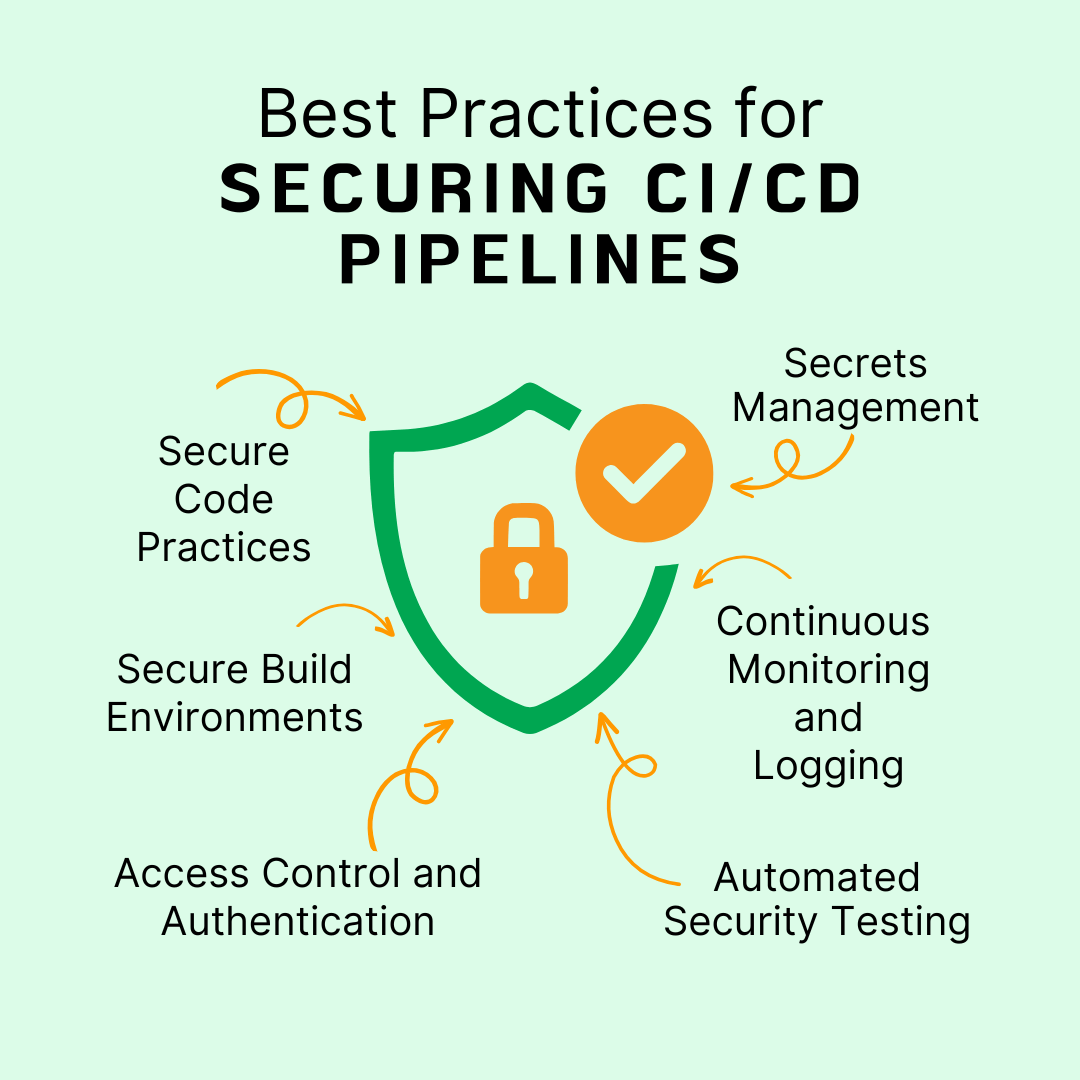
Best Practices for Securing CI/CD Pipelines
Securing CI/CD pipelines is essential to protect against potential threats and ensure the integrity of the development and deployment processes. Here are key best practices to enhance security:
Secure Code Practices
- Code Review and Static Analysis: Regular code reviews and static analysis help identify vulnerabilities early. Implement automated tools to scan code for security flaws before it enters the pipeline, reducing the risk of introducing vulnerabilities.
- Implementing Secure Coding Standards: Adhering to secure coding practices ensures that all code produced is less likely to have security issues. Establish and enforce coding standards that address common security pitfalls.
Secure Build Environments
- Isolating Build Environments: Use isolated environments for building and testing code to prevent cross-contamination from other projects or external threats. This isolation limits the impact of any potential security issues to the specific environment.
- Using Immutable Infrastructure: Deploy immutable infrastructure where each build or deployment uses a fresh environment. This approach minimizes the risk of configuration drift and ensures consistency across environments.
Access Control and Authentication
- Role-Based Access Control (RBAC): Use RBAC to grant users only the permissions they need. Restrict access to sensitive pipeline components and repositories based on roles, minimizing the risk of unauthorized access.
- Multi-Factor Authentication (MFA): Implement multi-factor authentication (MFA) for accessing CI/CD tools and repositories. This extra layer of security strengthens protection by making it more difficult for attackers to compromise accounts using passwords alone.
Secrets Management
- Encrypting Secrets and API Keys: Securely store secrets, credentials, and API keys through encryption. Refrain from hard-coding these values in source code or configuration files to protect them from exposure.
- Using Secure Vaults: Utilize dedicated secrets management solutions, such as HashiCorp Vault, to handle sensitive information securely. These tools offer secure storage and access controls for essential confidential information.
Continuous Monitoring and Logging
- Implementing Monitoring Tools: Deploy monitoring tools to track activity across your CI/CD pipelines. Real-time monitoring helps detect anomalies and potential security breaches quickly.
- Centralized Logging for Threat Detection: Aggregate logs from various sources into a centralized system for analysis. This approach enables effective threat detection and incident response by providing a comprehensive view of pipeline activities.
Automated Security Testing
- Integrating Security Testing Tools: Integrate security testing tools like Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) within the CI/CD pipeline. Automating the testing process helps identify vulnerabilities early in development.
- Regular Vulnerability Scanning: Perform regular vulnerability scans to detect and address potential security issues in your applications and infrastructure. Schedule these scans to occur automatically as part of the CI/CD process.
Tools and Technologies for Securing CI/CD
Securing CI/CD pipelines requires leveraging a range of tools and technologies designed to address various aspects of the security landscape. Here’s an overview of important tools and technologies to consider:
CI/CD Tools with Security Features
- Jenkins: A widely used CI/CD tool, Jenkins offers various security plugins and features. Ensure that Jenkins is configured with appropriate security settings, such as role-based access control and secure plugin management, to protect against vulnerabilities.
- GitLab CI/CD: GitLab provides built-in security features such as automated code scanning and vulnerability management, allowing you to detect issues early in the development process using its security tools.
- CircleCI: CircleCI supports integration with security tools and provides features for secure environment management. Leverage its security integrations to monitor and protect your CI/CD workflows.
Security Tools and Integrations
- Snyk: Snyk specializes in identifying and fixing vulnerabilities in open-source dependencies and container images. Integrate Snyk into your CI/CD pipeline to automatically scan for vulnerabilities and receive practical remediation recommendations.
- SonarQube: SonarQube is a tool that evaluates code quality and security through static code analysis, identifying security vulnerabilities and code smells. Integrating it into your CI/CD pipeline improves both the security and quality of your code.
- Aqua Security: Aqua Security offers robust solutions for container security, featuring vulnerability scanning and runtime protection. Utilize Aqua Security tools to protect containerized applications throughout the entire CI/CD lifecycle.
Best Practices for Tool Configuration
- Secure Plugin Management: Regularly review and update plugins and integrations to mitigate vulnerabilities. Disable unused plugins and ensure that all plugins are from trusted sources.
- Updating and Patching Tools: Ensure all CI/CD tools are consistently updated with the latest patches. Regularly review security advisories and promptly apply updates to mitigate known vulnerabilities.
Integrating Security into CI/CD Pipelines
Integrating security into CI/CD pipelines is essential for safeguarding the software development lifecycle. By incorporating security practices early and continuously throughout the process, organizations can better protect their applications and infrastructure. Here’s how to effectively integrate security:
Incorporating Security into the Development Workflow
- Shift Left Security: Emphasize security from the earliest stages of development by integrating security practices into the initial phases of the CI/CD pipeline. This approach, known as "shift left", ensures that security issues are identified and addressed before code progresses too far, reducing the cost and complexity of remediation.
- Security Gates in Pipelines: Implement security gates within the CI/CD pipeline to enforce security policies and standards. These gates can automatically halt the pipeline if vulnerabilities are detected, preventing potentially insecure code from reaching production.
Training and Awareness for Development Teams
- Regular Security Training: Provide ongoing security training for development teams to ensure they are aware of the latest threats and best practices. This training helps developers write secure code and recognize potential vulnerabilities.
- Creating a Security-First Culture: Foster a security-first mindset across the development team by integrating security considerations into daily workflows and decision-making processes. Encourage collaboration between development and security teams to build a culture where security is a shared responsibility.
Real-Life Case Studies
Secure CI/CD Implementation in a Large Enterprise
Company: IBM
Challenge: IBM, a leader in technology and consulting, faced challenges securing its CI/CD pipeline due to its vast and complex software infrastructure.
Solution: IBM implemented a multi-faceted approach to enhance pipeline security. They utilized Jenkins with a comprehensive set of security plugins, integrated automated vulnerability scanning tools like SonarQube and Snyk, and enforced role-based access control (RBAC) and multi-factor authentication (MFA). They also isolated build environments and adopted immutable infrastructure to prevent unauthorized access and reduce the risk of contamination.
Outcome: IBM significantly improved the security of its CI/CD pipelines, reducing vulnerabilities and ensuring that potential threats were identified and mitigated early in the development process.
Lessons Learned from a Security Breach in CI/CD
Company: Capital One
Incident: In 2019, Capital One suffered a data breach due to a vulnerability in its CI/CD pipeline. The breach was caused by a misconfigured firewall and inadequate security measures around sensitive data in their AWS environment.
Response: Following the breach, Capital One took decisive action to bolster their security. They implemented enhanced security measures, including stronger secrets management practices using AWS Secrets Manager, improved configuration management, and automated security gates in their CI/CD pipelines to catch vulnerabilities before deployment. Additionally, they focused on upskilling their development team with advanced security training.
Outcome: These measures led to a more secure and resilient CI/CD pipeline. Capital One’s approach to addressing the breach set a precedent for how to effectively respond to and learn from security incidents.
Key Takeaways
- Embed Security Early: Integrate security practices into the initial stages of the CI/CD pipeline to identify and address vulnerabilities early (shift left security).
- Automate Security Checks: Use automated tools for code scanning, vulnerability detection, and secrets management to enhance security within the CI/CD pipeline.
- Implement Access Controls: Utilize role-based access control (RBAC) and multi-factor authentication (MFA) to secure access to CI/CD tools and environments.
- Isolate and Secure Environments: Adopt isolated build environments and immutable infrastructure to minimize security risks and protect against contamination.
- Continuous Monitoring and Training: Regularly monitor pipeline activities and provide ongoing security training to development teams to maintain a strong security posture.
Conclusion
Securing CI/CD pipelines is essential in today’s fast-paced development landscape, where rapid delivery and complex applications increase vulnerability risks. By integrating robust security practices early in the CI/CD process, organizations can effectively mitigate these risks and safeguard their software.
Key practices include shifting security left by incorporating it into early development stages, automating security checks, and enforcing strict access controls. Utilizing tools for automated code scanning, secrets management, and vulnerability detection further strengthens defenses. Real-life examples from companies like IBM and Capital One highlight the effectiveness of these strategies in preventing and addressing security issues.
Additionally, fostering a security-first culture and providing ongoing training for development teams ensures that security is consistently prioritized and applied. As threats evolve, staying adaptable and embracing emerging technologies will be crucial for maintaining resilience.

