Introduction
In today's digital landscape, traditional security models fall short as cyber threats evolve. Many organizations rely on outdated perimeter-based defenses, leaving critical assets vulnerable.
This escalating risk demands a radical shift. Enter the Zero Trust Security Model, an approach where no one is trusted by default, and every access request is verified. This model offers a robust solution to safeguarding sensitive data and fortifying your security posture against modern threats.
Understanding Zero Trust
Zero Trust is a security model that shifts away from traditional perimeter-based defenses by operating under the principle of never trust, always verify. Under a Zero Trust framework, all users, devices, and applications—regardless of their location—must undergo authentication, authorization, and ongoing verification before accessing any resources.
This model relies on principles such as least privilege, micro-segmentation, and strict identity verification to minimize risks and protect sensitive data. By treating every access request as a potential threat, Zero Trust helps organizations reduce attack surfaces and prevent unauthorized access.
This approach is particularly effective in today's environment, where remote work, cloud computing, and mobile devices have blurred the traditional network boundaries, making it crucial to maintain stringent security controls at every level.
Implementing Zero Trust requires a cultural shift within organizations, as it demands continuous monitoring and verification, ensuring that security is maintained without compromising usability. The result is a more resilient and adaptive security posture, capable of defending against modern cyber threats.
Benefits of Zero Trust Security Model
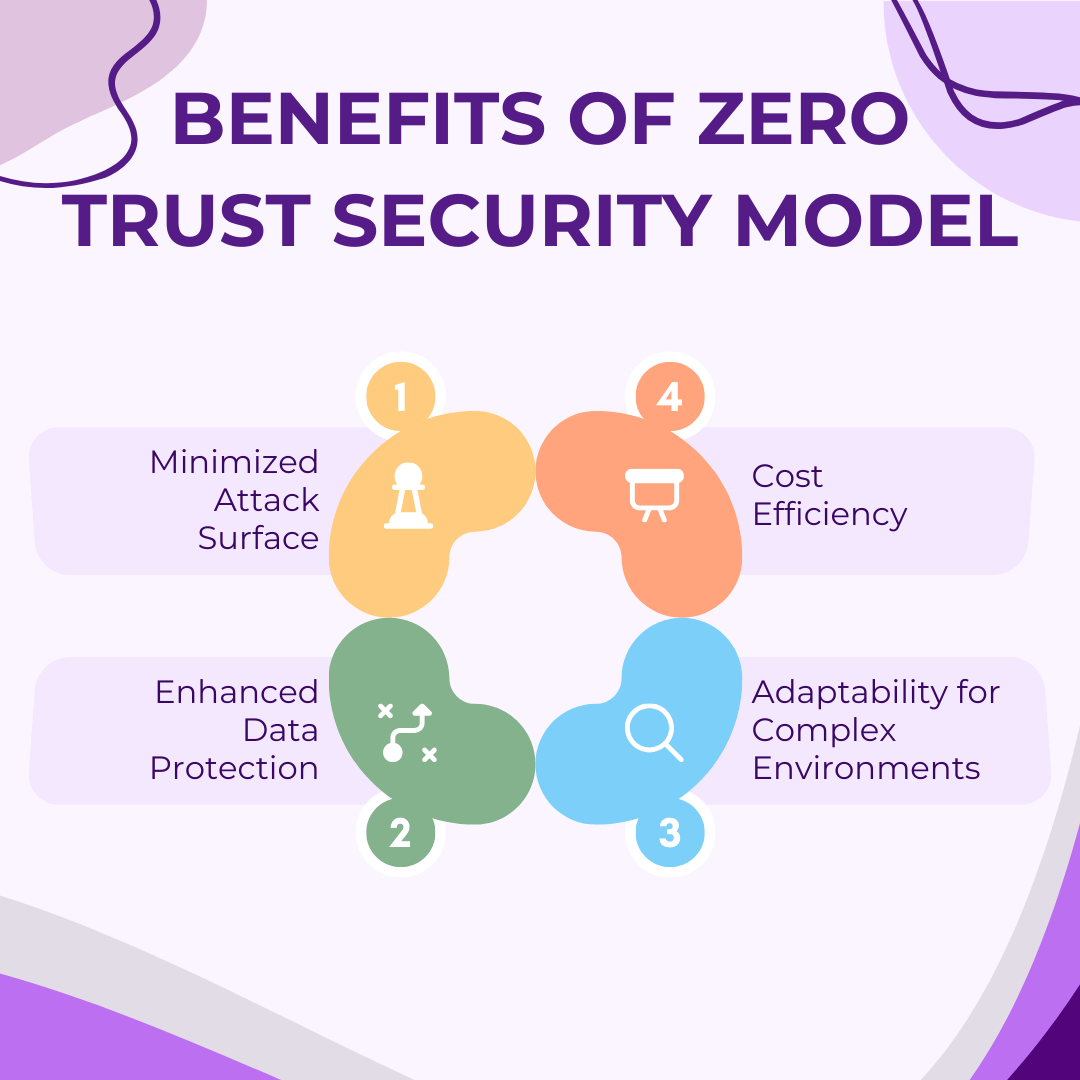
Adopting a Zero Trust Security Model offers several key benefits that significantly enhance an organization’s security posture.
First, it reduces the attack surface by ensuring that no entity is inherently trusted, which minimizes the risk of unauthorized access. This model also improves data protection by enforcing strict access controls and continuous monitoring, ensuring that sensitive information remains secure.
Additionally, Zero Trust is adaptable, making it ideal for organizations with diverse and evolving IT environments. Finally, it provides a cost-effective solution by potentially lowering long-term security expenditures through more efficient and targeted security measures.
Challenges in Adopting Zero Trust
Implementing the Zero Trust Security Model comes with a range of challenges that organizations need to address.
One of the primary hurdles is the cultural shift required within an organization, as Zero Trust demands a mindset change from implicit trust to continuous verification, which can face resistance.
Additionally, integrating Zero Trust into existing IT infrastructures can be complex, particularly in environments with legacy systems. The model also requires substantial initial investment in technology, resources, and staff training, which may strain budgets and operational capacity.
However, these challenges are surmountable with a phased and strategic approach, leading to a stronger security posture in the long run.
Implementation Strategy
Adopting a Zero Trust Security Model calls for a well-planned, step-by-step strategy. Begin with a thorough evaluation of your existing security framework to uncover weaknesses and pinpoint areas that need enhancement.
Engage key stakeholders early to gain buy-in and align on goals. Next, prioritize high-value assets and critical systems for initial deployment. Choose the right technology stack, including identity management, multifactor authentication, and network segmentation tools.
Gradually expand Zero Trust policies across the organization, ensuring continuous monitoring and refinement. Finally, invest in ongoing training to build a security-first culture and ensure successful adoption.
Case Studies
Examining real-world case studies of organizations that have implemented the Zero Trust Security Model provides valuable insights into the benefits and challenges of this approach.
For instance, a major financial institution successfully reduced its attack surface by deploying Zero Trust principles, leading to a significant drop in security incidents.
In another example, a healthcare provider enhanced patient data protection while maintaining compliance with regulatory requirements.
These case studies underscore the importance of a tailored implementation strategy and highlight the adaptability of Zero Trust across various industries.
Future of Zero Trust Security Model
The future of the Zero Trust Security Model is poised for significant evolution as cyber threats become more sophisticated.
Advances in artificial intelligence (AI) and machine learning (ML) will enhance Zero Trust by enabling automated threat detection and response, making security more proactive.
Additionally, as cloud adoption and remote work continue to rise, Zero Trust will play a critical role in securing decentralized networks.
The model will also likely influence future cybersecurity regulations, pushing organizations to adopt more stringent security practices to stay compliant and protect their digital assets.
Key Takeaways
- Zero Trust Basics: Shifts security from perimeter-based to continuous verification of every access request.
- Key Benefits: Reduces attack surfaces, enhances data protection, and adapts to evolving IT environments.
- Implementation Challenges: Requires cultural change, integration with existing systems, and significant resource investment.
- Strategic Rollout: Start with critical assets, engage stakeholders, and expand gradually with ongoing monitoring.
- Future Trends: AI and ML will drive automation, with Zero Trust becoming essential for securing decentralized networks and meeting regulatory demands.
Conclusion
In conclusion, the Zero Trust Security Model signifies a significant change in the way organizations secure their digital assets. By adopting a never trust, always verify approach, it significantly strengthens security against modern cyber threats.
While the implementation of Zero Trust can be challenging, the benefits, such as reduced attack surfaces, enhanced data protection, and improved adaptability make it a worthwhile investment. As technology advances and cyber threats evolve, Zero Trust will continue to play a critical role in safeguarding networks and ensuring regulatory compliance.

