Choose a different version or distribution
Introduction
Before we begin talking about how to set up an object storage server using MinIO on Ubuntu 20.04, let’s briefly understand – What is MinIO?
MinIO is an open-source object storage for efficient data management. It is self-hosted object storage system for easy and efficient data storage and distribution. Its flexible architecture and compatibility with Amazon S3 make it highly versatile for businesses of all sizes.
With MinIO, you can easily deploy it on-premises or in the cloud, ensuring total control over your data while benefiting from high reliability and scalability. Experience hassle-free storage management with MinIO user-friendly interface and comprehensive documentation.
In this tutorial, you will set up an Object Storage Server Using MinIO on Ubuntu 20.04. We will also address a few FAQs on how to set up an Object Storage Server Using MinIO on Ubuntu 20.04.
Advantages of MinIO
- Open-source: MinIO is open-source, allowing for customization and community-driven development.
- Self-hosted: It provides the flexibility to host and manage your data storage infrastructure as per your requirements.
- Scalability: MinIO enables easy scalability, allowing you to expand your storage as your needs grow.
- Compatibility: It is compatible with Amazon S3, ensuring smooth integration with existing S3-compatible applications and tools.
- User-friendly: MinIO offers a user-friendly interface and comprehensive documentation for hassle-free storage management.
Prerequisites
- Ubuntu 20.04 64-bit operating system
- A user account with sudo privileges
- Command-line/terminal
You will be needing a domain name in this tutorial, you can purchase one or can use a free domain name. In this tutorial, we will be addressing your domain as your_domain.
Step 1 - Install and Configure the MinIO Server
1) Firstly, you need to install and configure the MinIO server through a precompiled binary.
- Login into your server by replacing
johnywith your username andyour_server_ipwith your Ubuntu 20.04 server’s IP address:
ssh johny@your_server_ip
2) After that, update the package database and upgrade your system.
sudo apt update && sudo apt upgrade -y
3) Now, download the deb file from the MinIO server’s official website:
wget https://dl.min.io/server/minio/release/linux-amd64/minio_20230629051228.0.0_amd64.deb
You must see the following output:
Output
--2023-06-30 10:57:35-- https://dl.min.io/server/minio/release/linux-amd64/minio_20230629051228.0.0_amd64.deb
Resolving dl.min.io (dl.min.io)... 178.128.69.202, 138.68.11.125
Connecting to dl.min.io (dl.min.io)|178.128.69.202|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 37578640 (36M) [application/vnd.debian.binary-package]
Saving to: ‘minio_20230629051228.0.0_amd64.deb’
minio_20230629051228.0.0_amd64.deb 100%[=======================================================================================================>] 35.84M 14.3MB/s in 2.5s
2023-06-30 10:57:37 (14.3 MB/s) - ‘minio_20230629051228.0.0_amd64.deb’ saved [37578640/37578640]
4) Now, install it using dpkg or apt :
sudo dpkg -i minio_20230629051228.0.0_amd64.deb
5) Now, let's make a new user and group, since the systemd looks for a user account and group called minio-user. Avoid running the MinIO server as root for security reasons:
sudo groupadd -r minio-user
sudo useradd -M -r -g minio-user minio-user -s /sbin/nologin
In this command, the -s flag means to set /sbin/nologin as the shell for minio-user. This is a shell that does not allow user login, which is not needed for minio-user. -M flag instructs not to create a home directory for that user. -g means to add that user to a given group. -r instructs to create a system user.
6) After that, you must create a directory to store files. MinIO servers later organize the objects you store as buckets in this storage location. We will name the directory as minio in this tutorial:
sudo mkdir /usr/local/share/minio
7) Now, let the minio-user get ownership of that directory:
sudo chown minio-user:minio-user /usr/local/share/minio
8) After that, create your MinIO configuration file at /etc directory:
sudo mkdir /etc/minio
9) Now, again, let's give ownership of that directory to minio-user, too:
sudo chown minio-user:minio-user /etc/minio
10) Meanwhile, create the environment file needed to modify the default configuration using Nano (you can use any text editor as you wish):
sudo nano /etc/default/minio
11) Now, set some important environment variables in your environment file by adding the following lines:
MINIO_ACCESS_KEY="minio"
MINIO_VOLUMES="/usr/local/share/minio/"
MINIO_OPTS="-C /etc/minio --address your_server_ip:9000"
MINIO_SECRET_KEY="miniostorage"
Now, change your_server_ip with your local IP address then save and close the file after making changes.
Step 2 - Configure the firewall for MinIO Server
1) First, activate access through the firewall to the MinIO server on the configured port. In this tutorial, that port will be port 9000.
- Firstly, add the rule:
- Now, activate the firewall:
- You must see the following output:
- To generate the following output, press
yandENTER:
sudo ufw allow 9000
sudo ufw allow 22
sudo ufw enable
Output
Command may disrupt existing ssh connections. Proceed with operation (y|n)?
Output
Firewall is active and enabled on system startup
Finally, your MinIO server is ready to accept the traffic! Start the MinIO server using the below command:
sudo systemctl start minio
Step 3 - Secure Access to Your MinIO Server With a TLS Certificate or Self-signed.
If you don't have a domain name, or you don't want https you can skip this step.
1) Firstly, open the port 80 to allow HTTP and HTTPS access through your firewall:
sudo ufw allow 80
2) Secondly, for HTTPS, open up port 443:
sudo ufw allow 443
3) Next, check the firewall status after adding these rules by running the following command:
sudo ufw status verbose
You must receive a similar output:
Output
Status: active
Logging: on (low)
Default: deny (incoming), allow (outgoing), disabled (routed)
New profiles: skip
To Action From
-- ------ ----
22/tcp (OpenSSH) ALLOW IN Anywhere
9000 ALLOW IN Anywhere
443 ALLOW IN Anywhere
80 ALLOW IN Anywhere
22/tcp (OpenSSH (v6)) ALLOW IN Anywhere (v6)
9000 (v6) ALLOW IN Anywhere (v6)
443 (v6) ALLOW IN Anywhere (v6)
80 (v6) ALLOW IN Anywhere (v6)
Now your port 443 and port 80 are open.
4) After that, you will install Certbot to maintain a separate PPA repository by adding it to your list of repositories:
- Firstly, install
software-properties-common, a package for managing PPAs: - Secondly, add the Universe repository:
- Now, it's time to add the Certbot repository:
sudo apt install software-properties-common
sudo add-apt-repository universe
sudo add-apt-repository ppa:certbot/certbot
You must see the following output:
Output
This is the PPA for packages prepared by Debian Let's Encrypt Team and backported for Ubuntu(s).
More info: https://launchpad.net/~certbot/+archive/ubuntu/certbot
Press [ENTER] to continue or ctrl-c to cancel adding it
Press ENTER and accept.
- Now, update the package list:
- Finally, install
certbot:
sudo apt update
sudo apt install certbot
5) Now, generate a new SSL certificate by using certbot:
- Use the
certonlycommand and--standaloneto obtain the certificate:
sudo certbot certonly --standalone -d minio-server.your_domain
You must see the following output:
Output
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Plugins selected: Authenticator standalone, Installer None
Enter email address (used for urgent renewal and security notices) (Enter 'c' to
cancel):
Press ENTER and add your email.
Certbot will then ask you to register with Let’s Encrypt:
Output
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please read the Terms of Service at
https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must
agree in order to register with the ACME server at
https://acme-v02.api.letsencrypt.org/directory
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(A)gree/(C)ancel:
Press ENTER and type A to agree.
Now you will be asked for your consent:
Output
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Would you be willing to share your email address with the Electronic Frontier
Foundation, a founding partner of the Let's Encrypt project and the non-profit
organization that develops Certbot? We'd like to send you email about our work
encrypting the web, EFF news, campaigns, and ways to support digital freedom.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o:
Once you answer Y or N, your public and private keys will be generated and saved in the /etc/letsencrypt/live/minio-server.your_domain_name directory.
6) Now, it's time to copy these two files (privkey.pem and fullchain.pem) into the certs directory under MinIO server configuration folder, which is /etc/minio for this tutorial. Use the following to copy privkey.pem and rename the file private.key:
sudo cp /etc/letsencrypt/live/minio-server.your_domain_name/privkey.pem /etc/minio/certs/private.key
7) After that, repeat the same with fullchain.pem, naming the result public.crt:
sudo cp /etc/letsencrypt/live/minio-server.your_domain_name/fullchain.pem /etc/minio/certs/public.crt
8) Now, change the ownership of the files to minio-user:
sudo chown minio-user:minio-user /etc/minio/certs/*
9) After that, to start using HTTPS, start the MinIO server:
sudo systemctl start minio
Step 4 - Secure Connection to MinIO's Web Interface Using HTTPS
1) First, connect to the MinIO web interface through HTTPS. You can access their web interface by pointing your browser to https://minio-server.your_domain:9000 or http://your_ip:9000.
Below, you can see the login screen of the MinIO server:
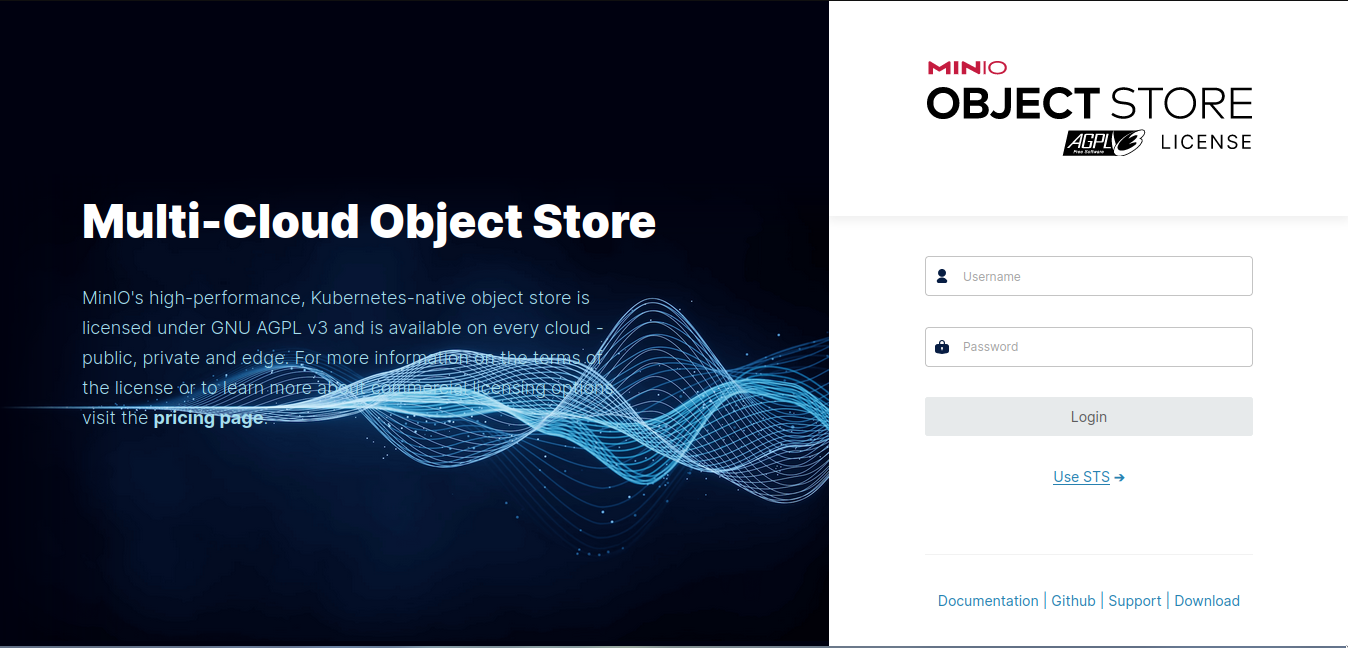
2) Now, you can log in by using your credentials. Enter the MINIO_ACCESS_KEY you set in the /etc/default/minio environment file in Step 1 for the Username. Enter the MINIO_SECRET_KEY you set in the same file for Password And click on login.
- Now, create a new bucket list where you can store objects, click on
Create a Bucketin the main interface.
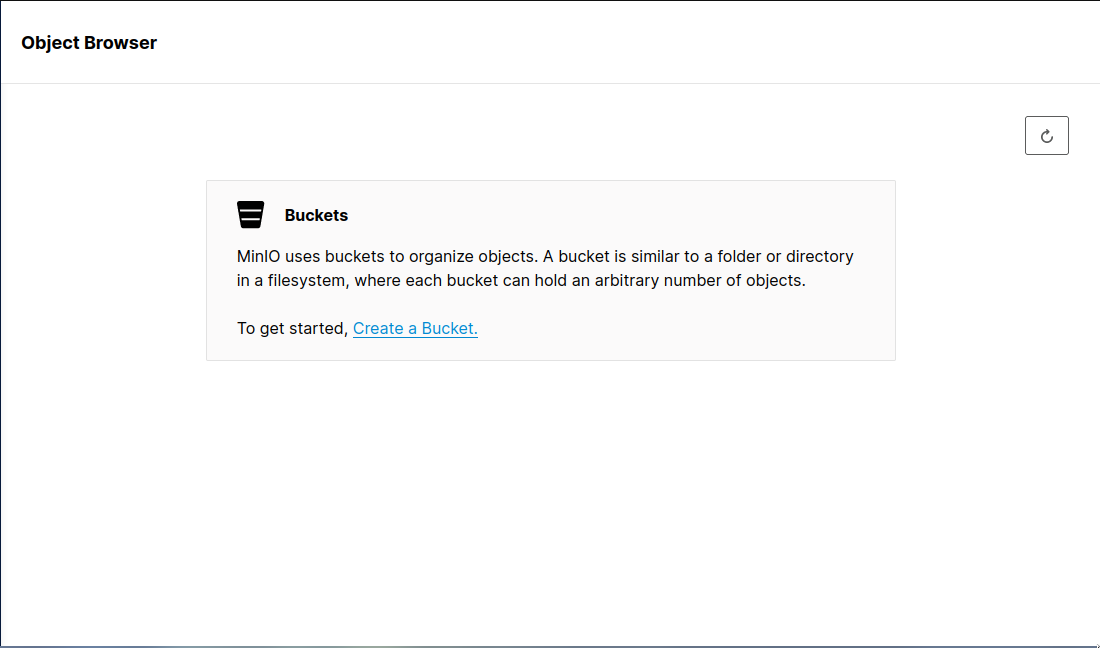
Now, enter a name for your new bucket in the prompt, check the radio button according to you, and then press ENTER key to save your progress
FAQs to Install and Use MinIO on Ubuntu 20.04
What are the hardware requirements for running MinIO?
MinIO is lightweight and can be run on a variety of hardware configurations. However, it is recommended to have sufficient disk space and memory for optimal performance.
Can I use MinIO in a distributed mode?
Yes, MinIO can be deployed in a distributed mode, allowing you to create a highly available and fault-tolerant storage infrastructure across multiple servers.
Is MinIO compatible with other object storage systems?
MinIO is compatible with the Amazon S3 API, making it compatible with a wide range of S3-compatible applications and tools.
How can I secure my MinIOserver?
MinIO supports TLS/SSL encryption, access control policies, and integration with identity providers like LDAP and OAuth, providing secure access to your data.
What happens if a node in the MinIO cluster fails?
MinIO automatically handles node failures, redistributing data across the available nodes to ensure data availability and reliability.
Can I set up automatic data backups with MinIO?
Yes, MinIO allows you to configure automatic data backups to remote storage, ensuring data redundancy and disaster recovery.
Is there a graphical user interface for managing MinIO?
Yes, MinIO provides a web-based graphical user interface (GUI) called "Minio Browser," which allows you to easily manage and interact with your data.
Conclusion
We hope this simple guide helped you understand how to set up an object storage server using MinIO on Ubuntu 20.04.
If you have any queries, please leave a comment below, and we’ll be happy to respond to them for sure.

